482/68 Friday, November 21, 2025
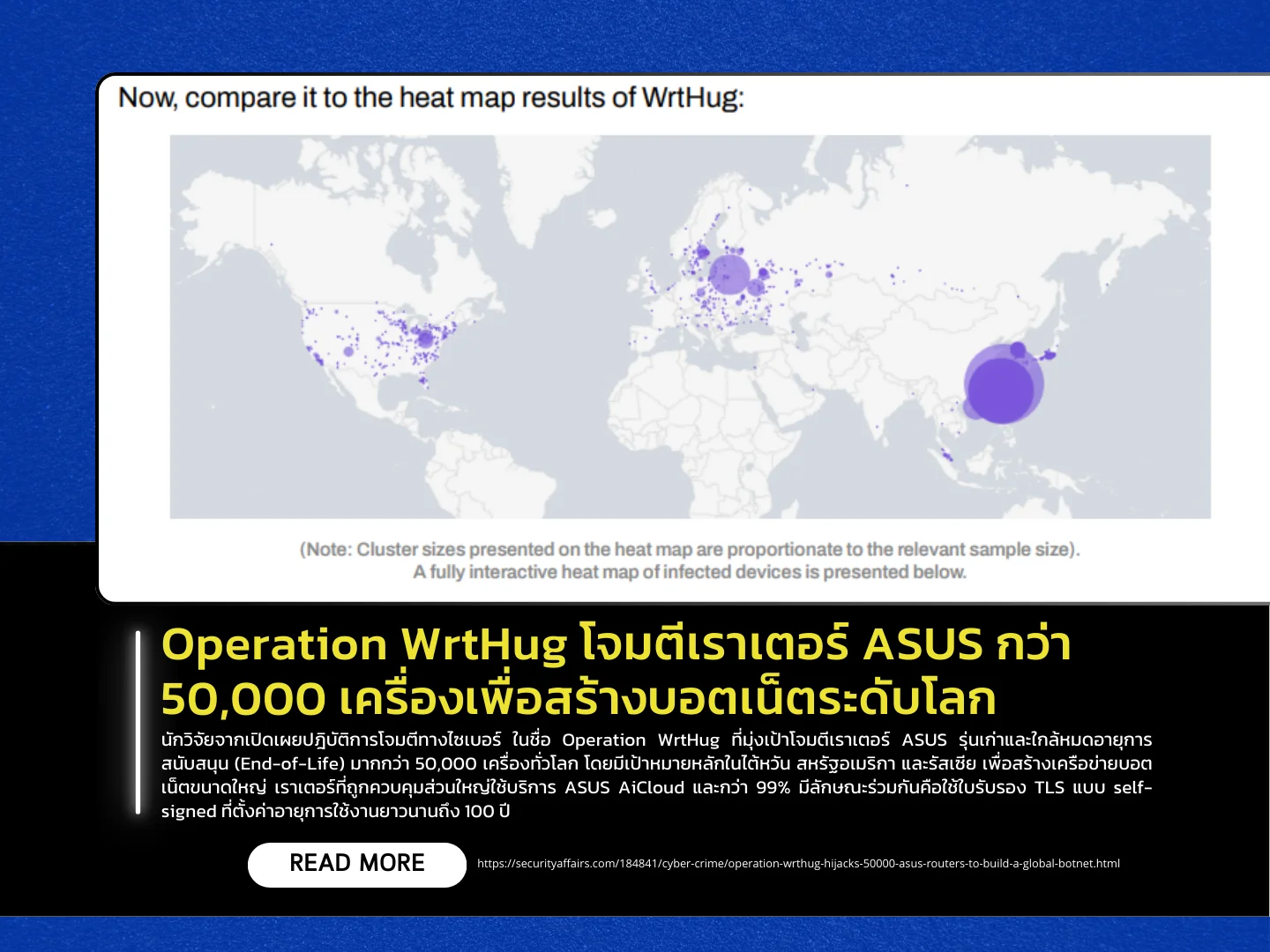
Researchers have uncovered a cyberattack campaign known as Operation WrtHug, which targets older and near end-of-life (EOL) ASUS routers-over 50,000 devices worldwide-with the goal of creating a massive botnet. The largest concentrations of compromised devices were found in Taiwan, the United States, and Russia. Most affected routers were using ASUS AiCloud, and over 99% shared a critical characteristic: they relied on self-signed TLS certificates configured with an unusually long validity period of 100 years.
Attackers exploited multiple vulnerabilities in outdated ASUS WRT routers, relying on nth-day vulnerabilities-security flaws that are already publicly disclosed but remain unpatched on many devices. Key vulnerabilities weaponized in the campaign include:
- CVE-2023-41345 to CVE-2023-41348 (OS command injection)
- CVE-2024-12912 (arbitrary command execution)
- CVE-2025-2492 (improper authentication)
The AiCloud service was used as the primary entry point, enabling attackers to take control of devices and enroll them into a large-scale botnet.
Experts believe the operation is linked to threat actors based in China, and may be coordinated with other botnets such as AyySSHush, which has previously targeted ASUS routers. The report underscores the serious risks posed by outdated and unsupported hardware that no longer receives security patches.
ASUS has confirmed that patches addressing all vulnerabilities exploited in Operation WrtHug have already been released. However, the company emphasizes that effective protection depends on administrators promptly applying updates or removing legacy devices from their networks.
