485/68 Monday, November 24, 2025
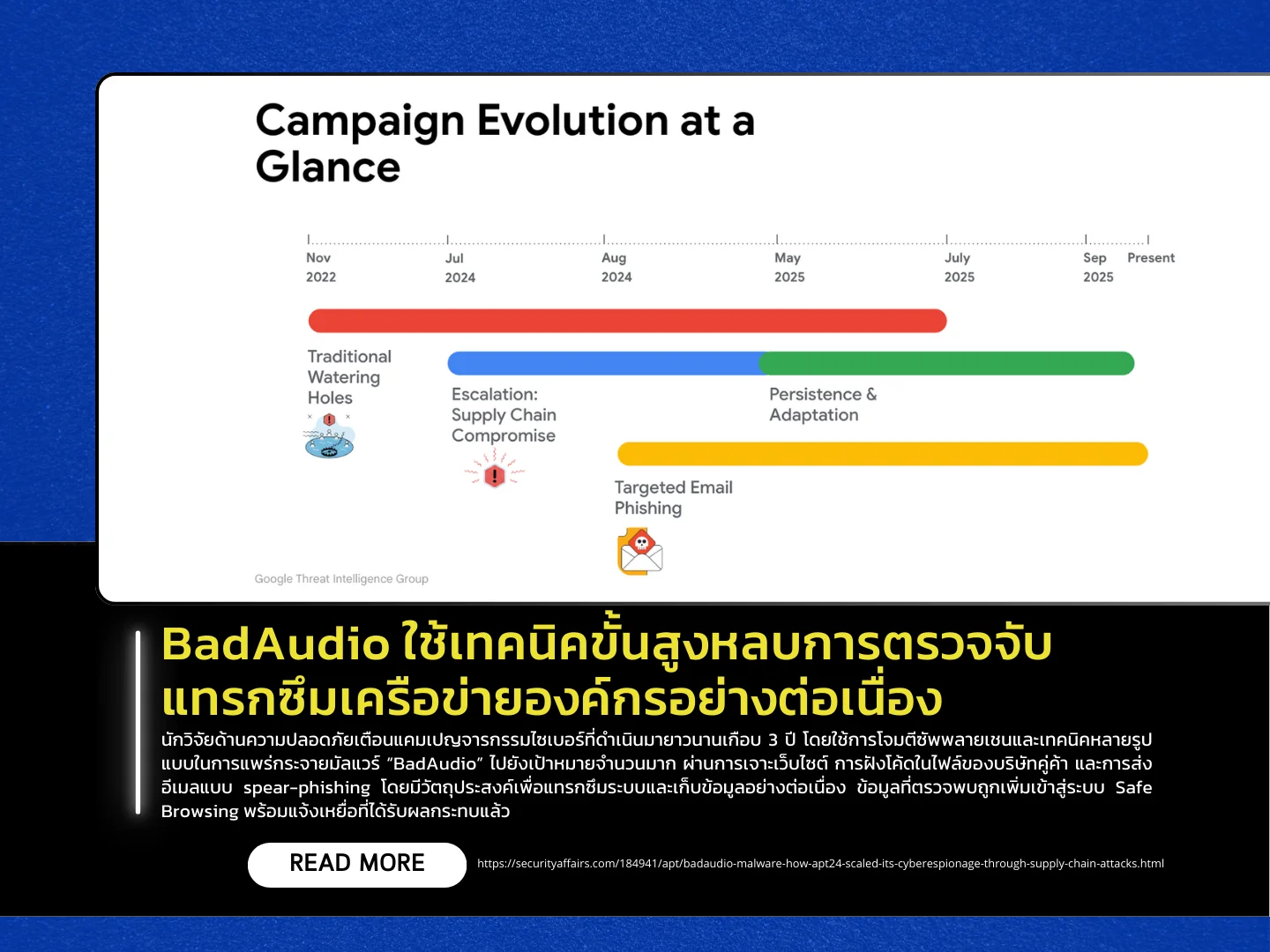
Security researchers are warning about a long-running cyber-espionage campaign-active for nearly three years-that leverages supply-chain attacks and multiple infection techniques to distribute the “BadAudio” malware to a wide range of targets. The attackers spread the malware through website compromises, embedding malicious code into files from partner companies, and highly targeted spear-phishing emails, with the goal of infiltrating networks and exfiltrating data over extended periods. Indicators identified in the campaign have been added to Safe Browsing, and affected victims have already been notified.
BadAudio functions as a first-stage downloader written in C++. It collects basic system information, encrypts it using AES, and hides the data inside Cookie values during requests for the next-stage payload from its command-and-control (C2) server. In many cases, the retrieved payload is a Cobalt Strike Beacon, decrypted using the same AES key. BadAudio also employs advanced evasion techniques such as control-flow flattening and DLL hijacking, making its behavior significantly harder to analyze.
Throughout the campaign, attackers continuously evolved their distribution methods. These include injecting malicious JavaScript into numerous websites to profile visitors before delivering fake update prompts, and compromising a digital-media service provider to insert malicious JS/JSON code into hundreds of customer domains. The report concludes that this campaign demonstrates the attackers’ strong capability to operate long-term, evade detection, and adapt their techniques to different environments.
