554/68 Monday, December 29, 2025
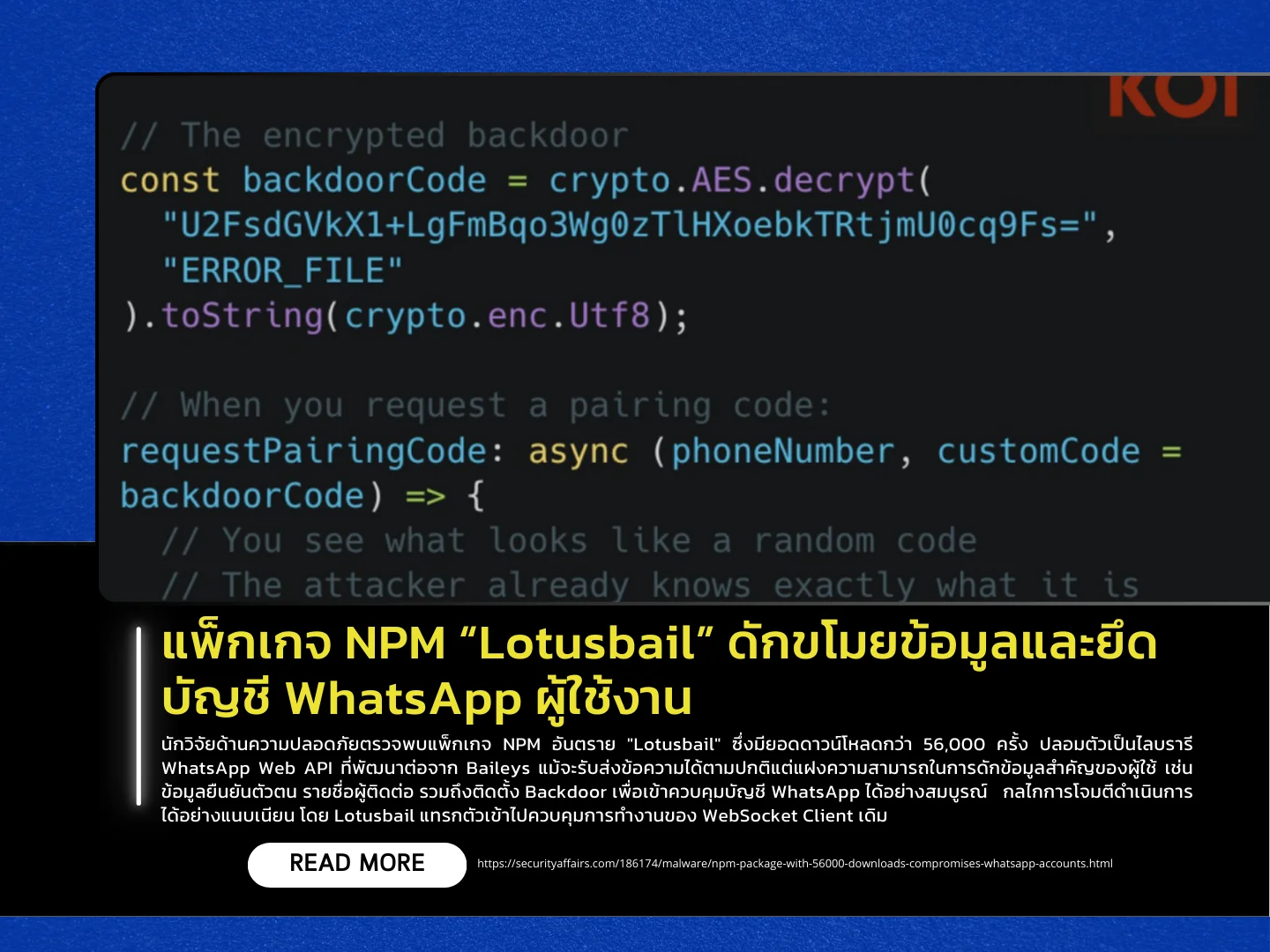
Cybersecurity researchers have identified a malicious NPM package named “Lotusbail”, which has been downloaded more than 56,000 times. The package masquerades as a WhatsApp Web API library built on top of Baileys. While it functions normally for sending and receiving messages, it secretly embeds capabilities to intercept sensitive user data, including authentication information and contact lists, and installs a backdoor that enables full takeover of WhatsApp accounts.
The attack mechanism operates in a highly stealthy manner. Lotusbail hooks into and controls the existing WebSocket client to intercept messages and media files, then exfiltrates the data using RSA encryption. It also embeds code that abuses the device pairing process, secretly linking an attacker-controlled device to the victim’s WhatsApp account. As a result, even if the package is later removed, attackers can retain persistent access to the account until the victim manually unlinks the unauthorized device.
The malware is particularly difficult to detect because it behaves like a legitimate library and includes 27 anti-debugging mechanisms designed to obstruct analysis. This makes traditional static code analysis or reputation-based checks, such as download counts, ineffective at identifying the threat. Experts warn that this case highlights a growing software supply chain risk, where effective detection requires behavioral analysis during runtime, rather than relying solely on static inspection.
