166/68 Tuesday, May 6, 2025
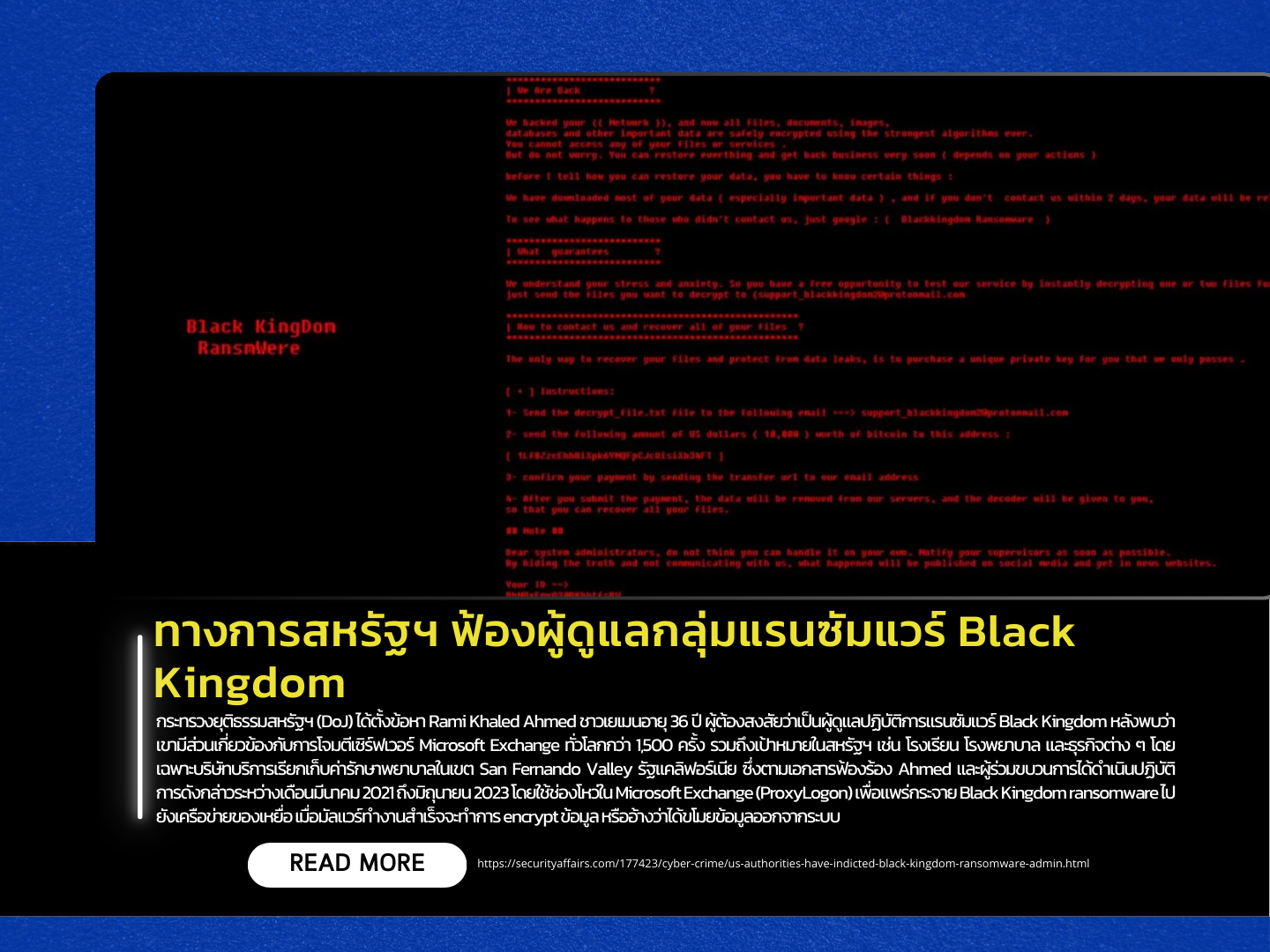
The U.S. Department of Justice (DoJ) has charged Rami Khaled Ahmed, a 36-year-old Yemeni national, suspected of operating the Black Kingdom ransomware campaign. Ahmed is accused of being involved in over 1,500 ransomware attacks on Microsoft Exchange servers worldwide, including targets in the United States such as schools, hospitals, and businesses. One notable victim was a medical billing services company based in California’s San Fernando Valley.
According to court documents, Ahmed and his associates carried out these attacks between March 2021 and June 2023 by exploiting the ProxyLogon vulnerability in Microsoft Exchange. Once inside a victim’s network, the Black Kingdom ransomware would either encrypt data or claim to have exfiltrated it, then display a ransom demand instructing victims to send $10,000 in Bitcoin to a designated cryptocurrency address and email proof of payment to the attackers.
Black Kingdom was first discovered in February 2020 by cybersecurity researcher GrujaRS. Initially, the ransomware was not fully functional—it left ransom notes but failed to encrypt files. However, later versions corrected these flaws and became capable of full-scale attacks. The group was known to exploit vulnerabilities in both Pulse Secure VPN and ProxyLogon to spread the malware. Their activities have been closely monitored by cybersecurity experts, including Marcus Hutchins.
Ahmed remains in Yemen and, if convicted, faces a maximum sentence of five years in prison per charge. The FBI, in coordination with New Zealand Police, continues to investigate and track the Black Kingdom group’s activities.
