221/68 Thursday, June 19, 2025
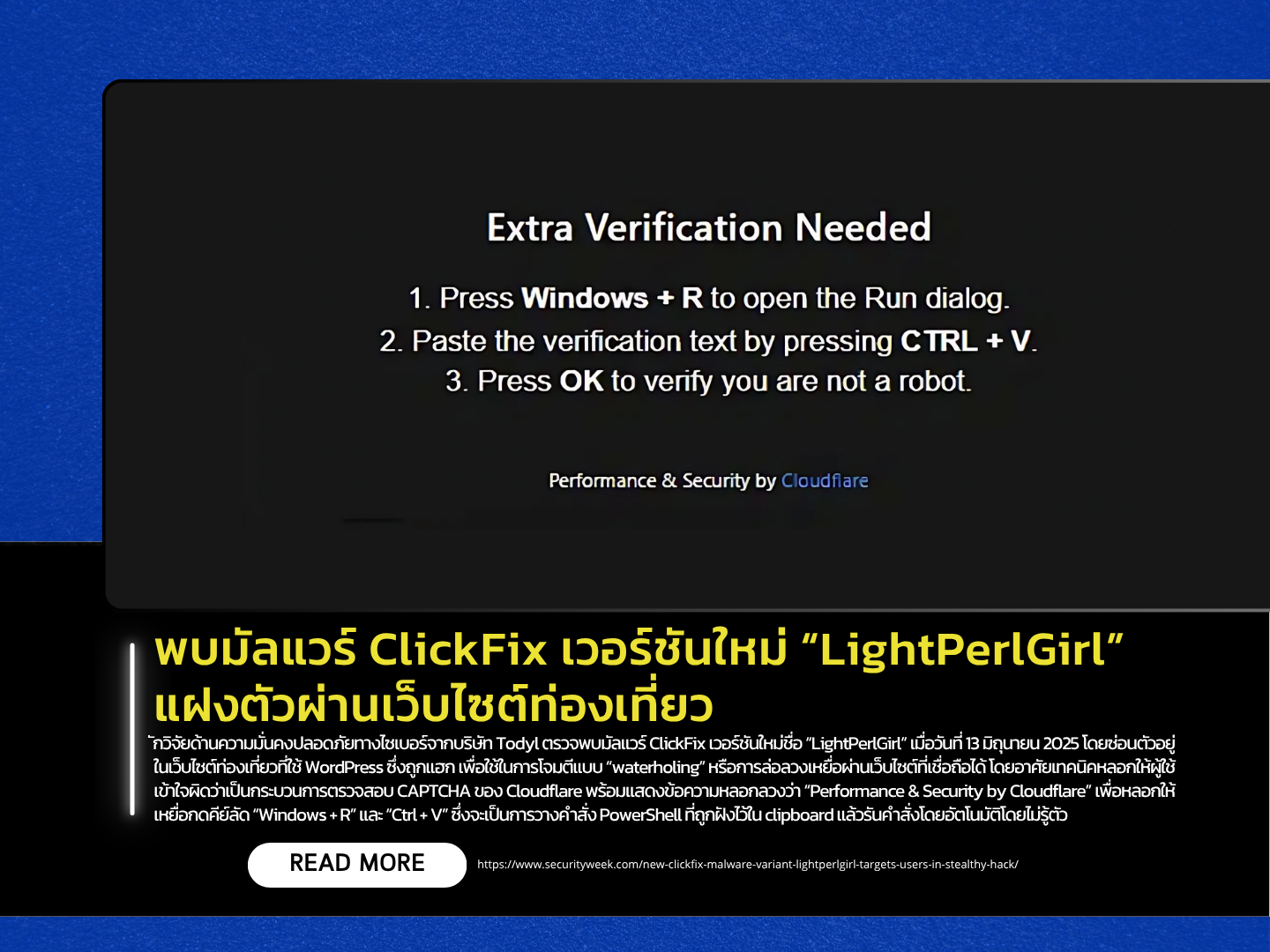
Cybersecurity researchers at Todyl have uncovered a new variant of the ClickFix malware, dubbed “LightPerlGirl”, on June 13, 2025. This variant was found embedded in a compromised WordPress-based travel website, used as part of a “waterholing” attack—a tactic where attackers lure victims through otherwise trusted websites. The site mimicked a Cloudflare CAPTCHA check, displaying a deceptive message reading “Performance & Security by Cloudflare”, and tricked users into pressing “Windows + R” followed by “Ctrl + V”. This sequence pastes a PowerShell command previously injected into the clipboard and executes it unknowingly.
The PowerShell command is heavily obfuscated to evade detection by both users and standard security tools. Once executed, it connects to a remote command-and-control (C2) domain to retrieve the actual malware payload—specifically, Lumma Infostealer, designed to steal sensitive user data including passwords and corporate network credentials. Researchers noted that ClickFix uses “Living off the Land Binaries” (LOLBINS) techniques, leveraging native Windows tools like PowerShell to carry out its attack without installing any foreign binaries, making it especially difficult to detect.
Interestingly, the malware variant is named “LightPerlGirl”, a name derived from the copyright string embedded in its code. While it remains unclear whether the developer of this version of ClickFix is affiliated with the Lumma group or represents a separate entity within the malware-as-a-service (MaaS) ecosystem, the fact that it can easily compromise home users without enterprise-grade protection poses a serious risk. Personal credentials belonging to executives or employees could later be weaponized to gain unauthorized access to larger corporate networks—a growing threat that cybersecurity agencies are urged to monitor closely.
