300/68 Wednesday, August 20, 2025
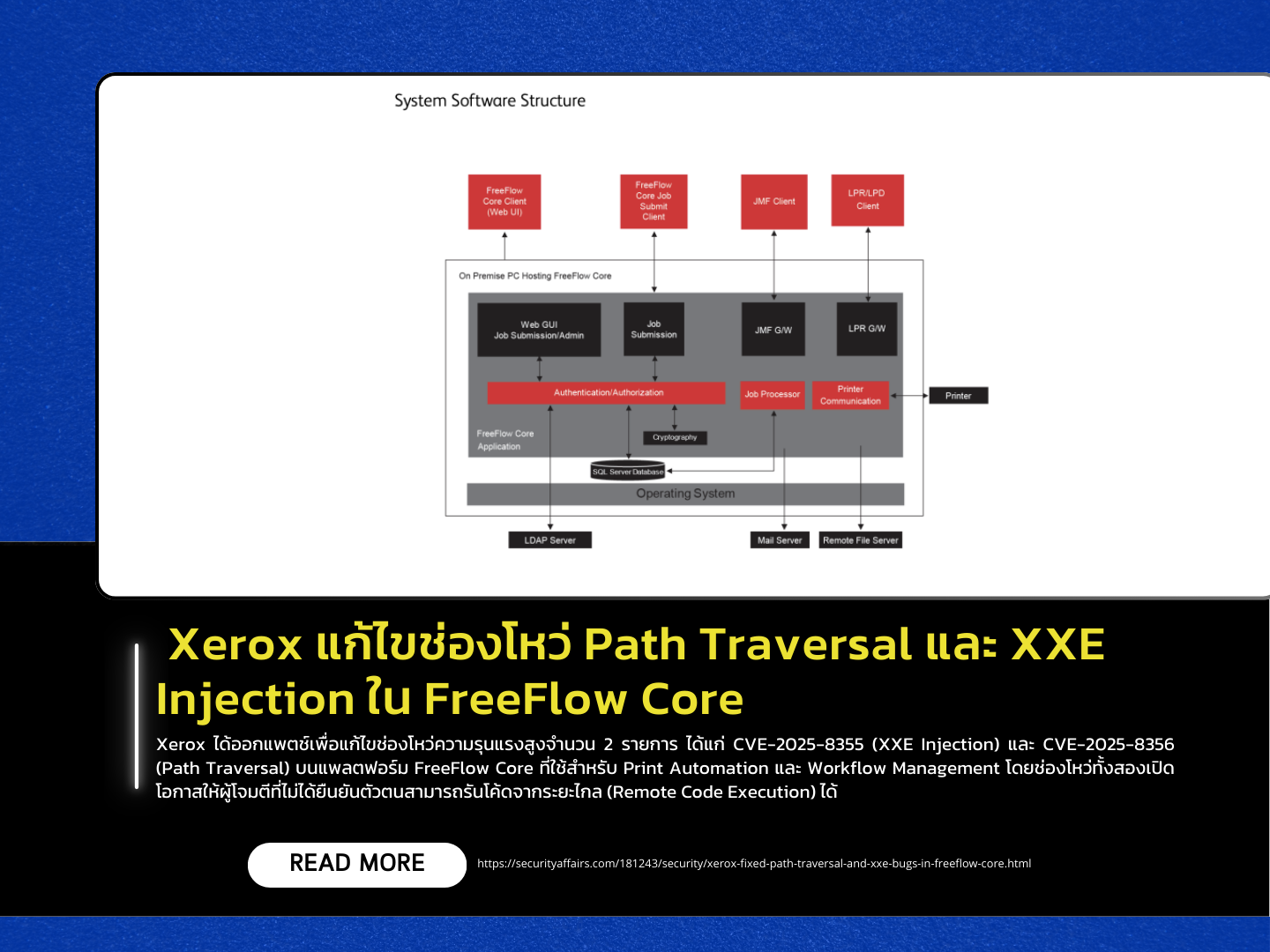
Xerox has released patches to address two high-severity vulnerabilities: CVE-2025-8355 (XXE Injection) and CVE-2025-8356 (Path Traversal) in its FreeFlow Core platform, which is used for Print Automation and Workflow Management. Both vulnerabilities allow unauthenticated attackers to perform remote code execution (RCE).
A research team from Horizon3 discovered the flaws. They reported that CVE-2025-8355 is located in the JMF Client Service of FreeFlow Core, which fails to adequately validate XML input, enabling attackers to conduct Server-Side Request Forgery (SSRF) attacks. On the other hand, CVE-2025-8356 is a Path Traversal vulnerability in the file management process that allows an attacker to place a webshell in an externally accessible location. When combined with JMF commands, this could lead to the execution of malicious payloads on vulnerable systems.
Xerox has fixed both vulnerabilities in FreeFlow Core version 8.0.5 and urges all users to update immediately. This is especially important because the platform is often used in organizations handling sensitive marketing data, which could be a prime target for cyber attackers.
