303/68 Friday, August 22, 2025
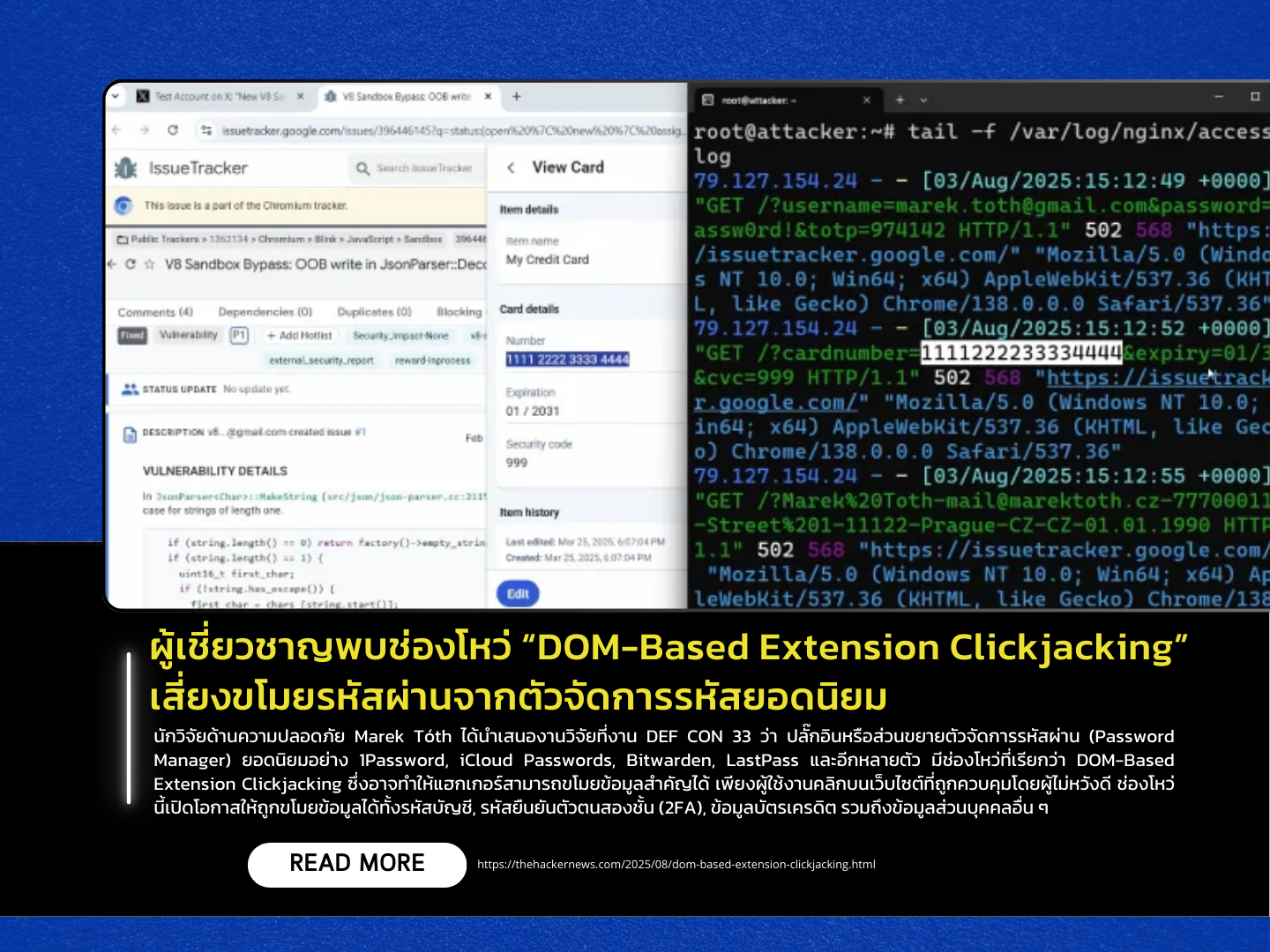
Security researcher Marek Tóth presented findings at DEF CON 33, revealing a newly identified vulnerability dubbed DOM-Based Extension Clickjacking that affects popular password manager browser extensions such as 1Password, iCloud Passwords, Bitwarden, LastPass, and several others. This flaw can potentially allow attackers to steal sensitive information simply by tricking users into clicking on elements of a maliciously crafted website. The attack can result in the theft of login credentials, two-factor authentication (2FA) codes, credit card details, and other personal data-posing a serious threat to the millions of users of these extensions.
The attack works by embedding malicious scripts in fake websites that exploit how password manager UIs, like auto-fill features, interact with web pages. These scripts can render login forms invisible (by setting opacity to zero), causing users to unintentionally trigger auto-fill when interacting with decoy pop-ups. Once triggered, the sensitive data is exfiltrated to the attacker’s server. Tóth’s tests showed that 10 out of 11 password manager extensions were vulnerable. In some cases, Passkey Authentication mechanisms were also susceptible.
As of now, six major vendors have yet to release patches: 1Password, Apple iCloud Passwords, Bitwarden, Enpass, LastPass, and LogMeOnce. Some are reportedly working on fixes, while others have downplayed the issue. In the meantime, experts recommend disabling auto-fill features, using copy-paste for credentials, and-especially for Chromium-based browser users-setting extensions to activate only on click (“On Click” setting), to minimize exposure until permanent fixes are deployed.
Source https://thehackernews.com/2025/08/dom-based-extension-clickjacking.html
