323/68 Thursday, September 4, 2025
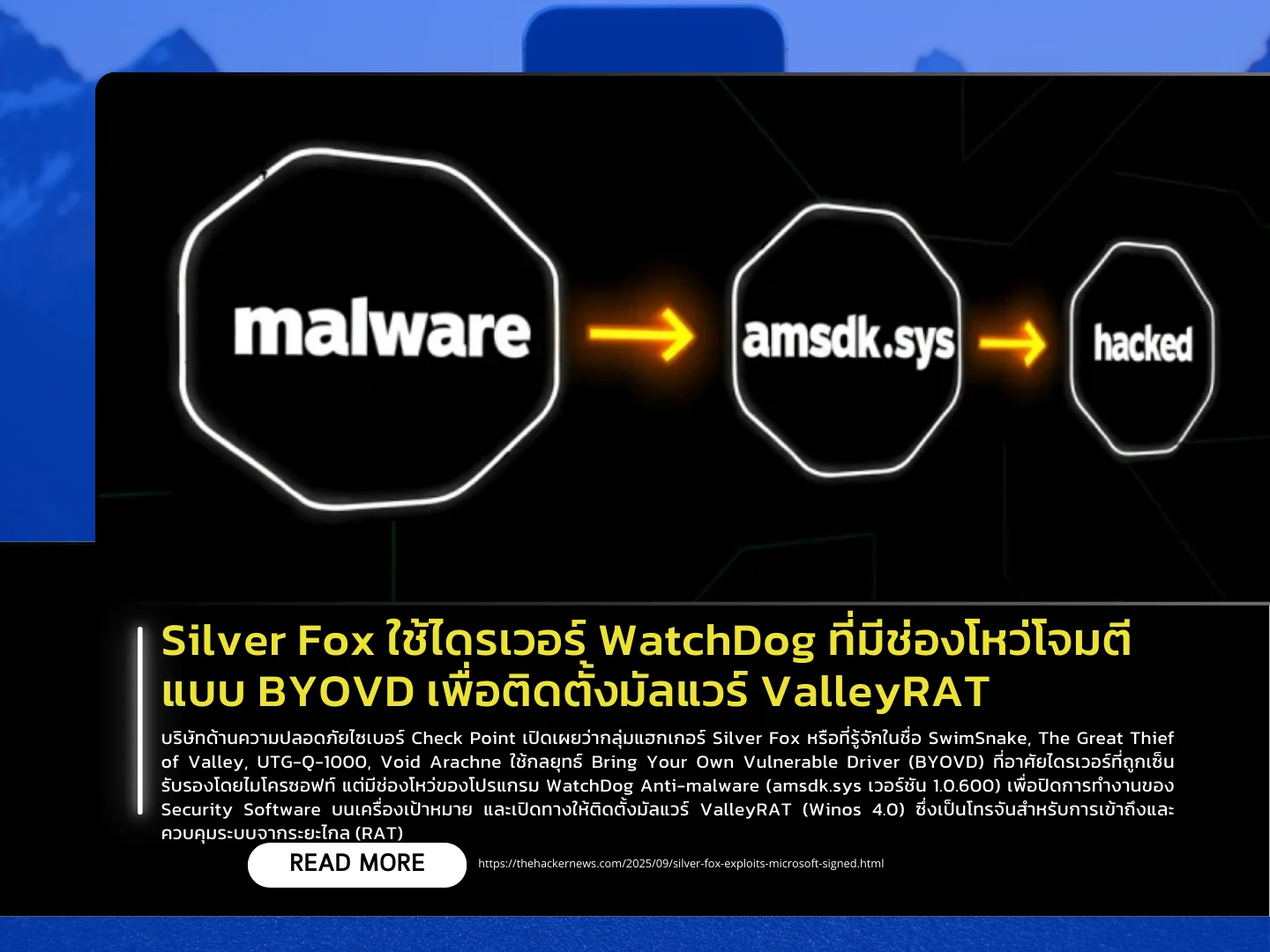
Cybersecurity company Check Point has revealed that the hacking group Silver Fox—also known as SwimSnake, The Great Thief of Valley, UTG-Q-1000, and Void Arachne—is using a Bring Your Own Vulnerable Driver (BYOVD) technique. The attackers leverage a Microsoft-signed but vulnerable driver from WatchDog Anti-malware (amsdk.sys version 1.0.600) to disable security software on targeted machines, clearing the way for the installation of ValleyRAT (Winos 4.0), a remote access trojan (RAT) designed for system compromise and control.
The attack method varies depending on the Windows version. On Windows 7, attackers exploit the known-vulnerable Zemana driver, while on Windows 10 and 11, they abuse the WatchDog driver, which has not yet been blocked by Microsoft. ValleyRAT is packaged in a single binary that includes anti-VM/anti-sandbox features, two drivers, an antivirus-disabling module, and a DLL downloader. Once executed, it connects to a C2 server to retrieve additional payloads.
Although WatchDog released version 1.1.100 to patch a local privilege escalation (LPE) flaw, it has not fixed the vulnerability that allows attackers to terminate arbitrary processes. Moreover, adversaries can modify just one byte of the driver file to generate a new hash without invalidating Microsoft’s digital signature, effectively bypassing blocklists. This demonstrates Silver Fox’s sophistication and adaptability. In addition to spreading ValleyRAT, the group operates subunits such as a Finance Group, which specifically targets financial professionals with phishing campaigns and fake websites to steal account credentials and conduct fraud—highlighting the escalating complexity and severity of cyber threats.
Source https://thehackernews.com/2025/09/silver-fox-exploits-microsoft-signed.html
