344/68 Tuesday, September 16, 2025
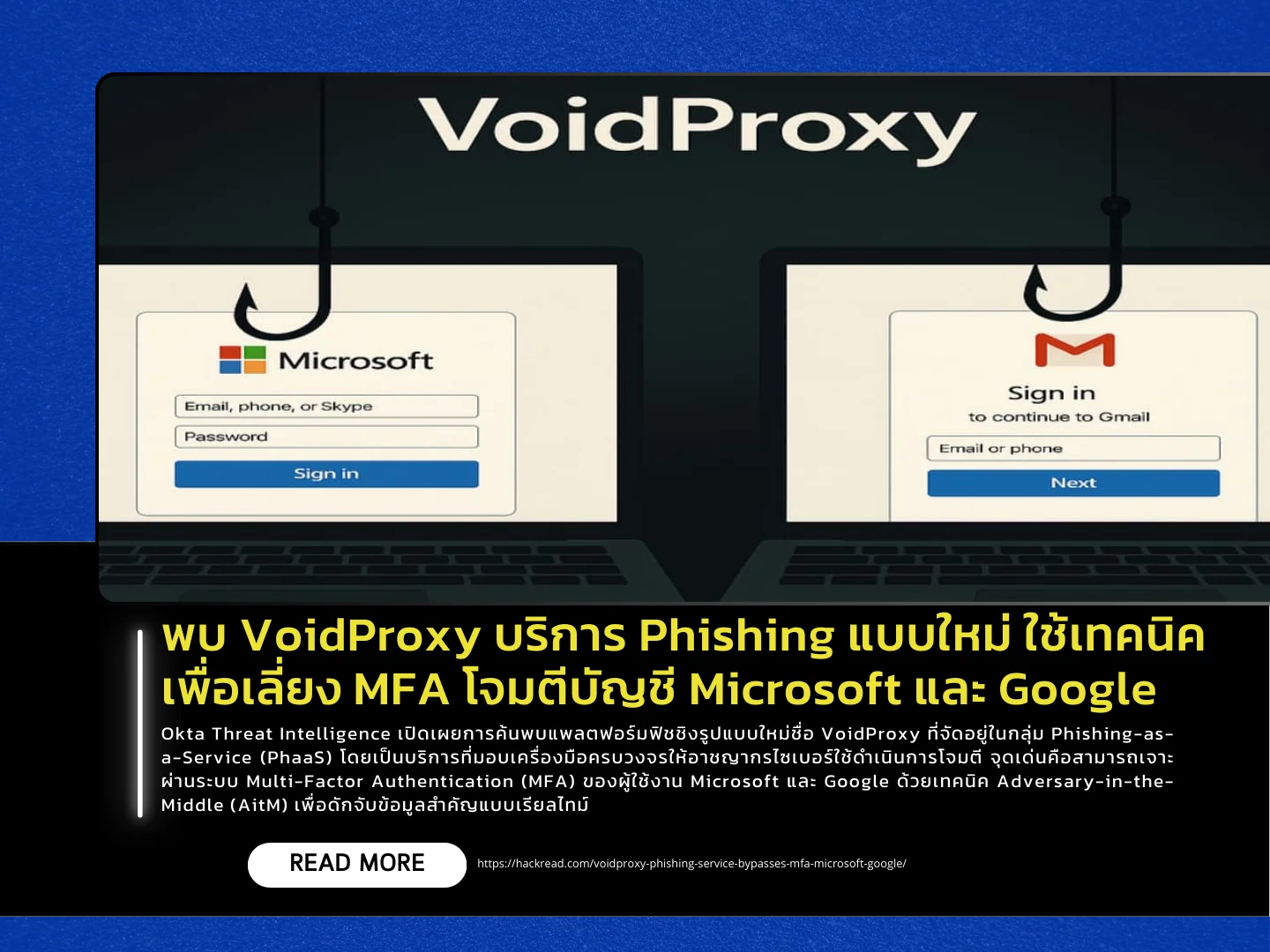
Okta Threat Intelligence has uncovered a new phishing platform called VoidProxy, categorized as Phishing-as-a-Service (PhaaS). It provides cybercriminals with a full toolkit to conduct attacks, with a key capability being its ability to bypass Multi-Factor Authentication (MFA) for Microsoft and Google accounts using an Adversary-in-the-Middle (AitM) technique to intercept sensitive data in real time.
According to a report dated September 11, 2025, Okta researchers noted that the attacks begin with phishing emails sent from compromised Email Service Provider (ESP) accounts such as Constant Contact, Active Campaign, or NotifyVisitors, allowing the messages to evade spam filters. When victims click the link, they are directed to a fake login page closely imitating Microsoft or Google. Once users enter their username, password, and MFA codes, VoidProxy intercepts the credentials and uses them to steal session cookies, enabling attackers to gain full access to the account as if they were the legitimate user-without further authentication.
Researchers found that VoidProxy is built with a two-layer architecture: a disposable front-end that can be discarded if detected, and a resilient back-end that remains active to sustain the attacks. It also employs multiple anti-analysis techniques, such as redirects, hijacked email accounts, and Cloudflare CAPTCHA to evade tracking. Stolen data is exfiltrated in real time to attackers via an admin panel and platforms like Telegram. Notably, VoidProxy was exposed after it failed to compromise accounts protected with Okta FastPass (a phishing-resistant authenticator), allowing researchers to fully reverse-engineer the platform’s architecture.
Source https://hackread.com/voidproxy-phishing-service-bypasses-mfa-microsoft-google/
