412/68 Monday, October 20, 2025
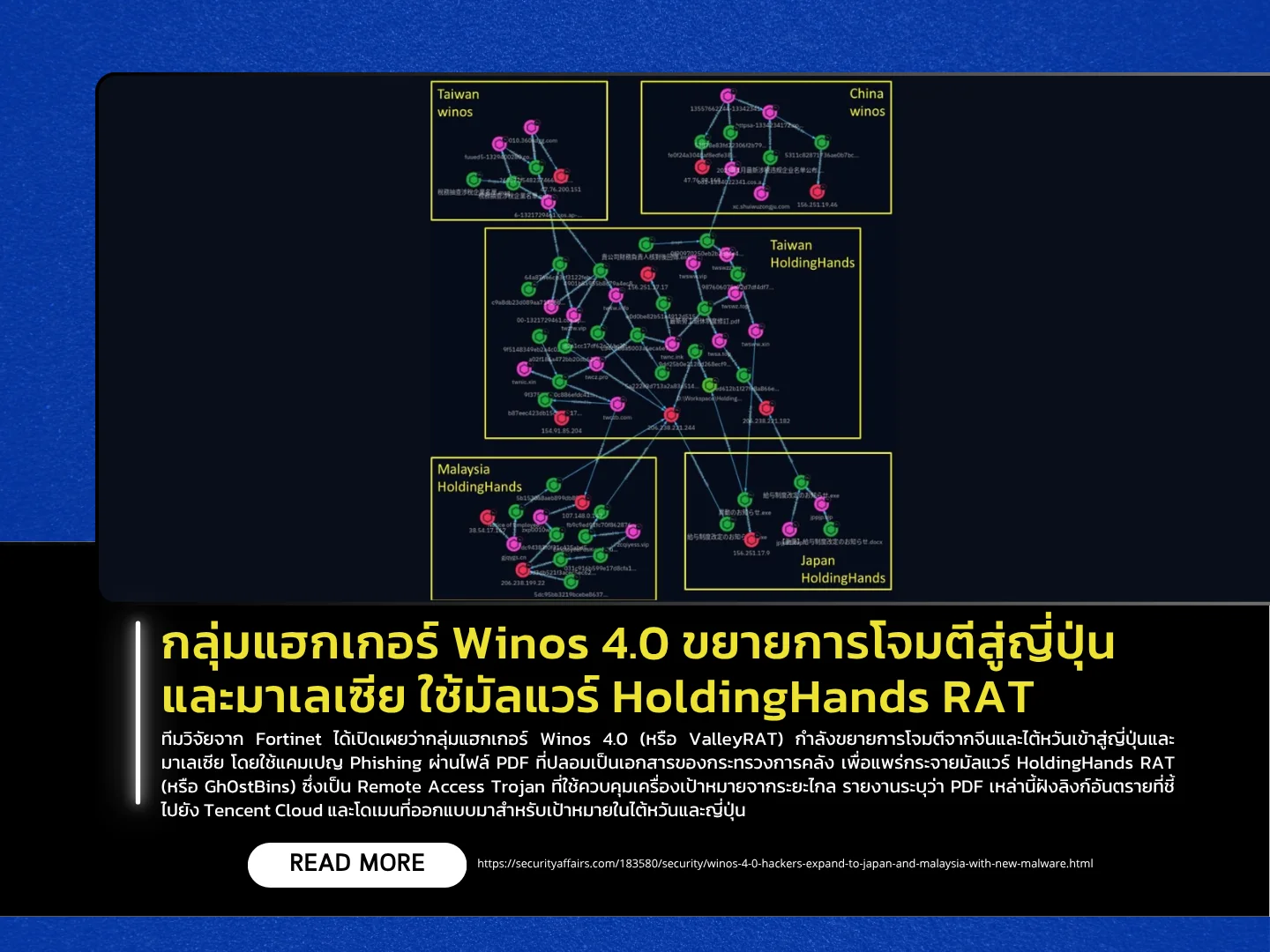
Researchers at Fortinet have revealed that the hacker group Winos 4.0 (also known as ValleyRAT) is expanding its operations from China and Taiwan into Japan and Malaysia, using phishing campaigns to distribute the HoldingHands RAT (also tracked as Gh0stBins), a Remote Access Trojan that enables remote control of compromised machines.
The report says the malicious PDFs are crafted to impersonate documents from finance ministries and embed links that point to Tencent Cloud and other domains tailored for targets in Taiwan and Japan. Some of the files impersonate draft tax regulations and redirect users to Japanese-language sites that deliver the HoldingHands RAT. The campaign uses multiple anti-detection techniques, such as digitally signing EXE files, hiding malicious links inside JSON data on dynamic pages, and an infrastructure that has been developed since 2024 with ties to phishing activity in China and Taiwan.
Analysis shows the malware operates in multiple stages and includes advanced capabilities. For persistence and stealth it uses Task Scheduler to load a malicious DLL (for example, TimeBrokerClient.dll) and injects payloads into trusted processes such as taskhostw.exe to reduce detection. The actors have also taken steps to evade major antivirus products (including Norton, Avast, and Kaspersky) and to update their C2 configuration dynamically—for example, by storing updated server IPs in Windows Registry keys. Researchers conclude the campaign demonstrates an escalation in phishing techniques combined with multi-stage malware delivery and cross-country infrastructure coordination across Asia.
