157/68 Tuesday, April 29, 2025
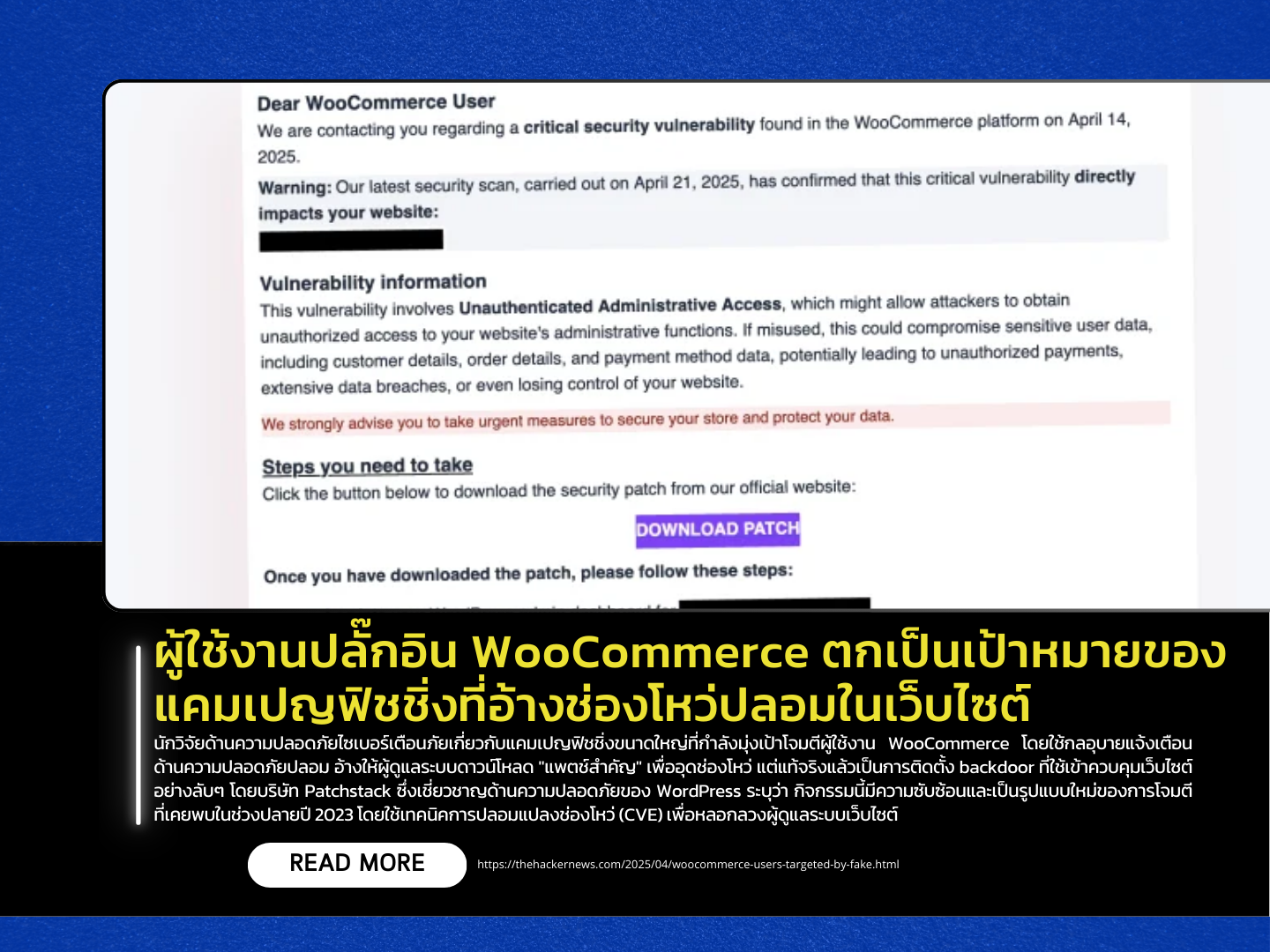
Cybersecurity researchers have issued a warning about a large-scale phishing campaign targeting WooCommerce plugin users by exploiting fake security alerts. The attackers are tricking website administrators into downloading a “critical patch” that instead installs a backdoor granting the attacker covert control over the site. Patchstack, a cybersecurity firm specializing in WordPress, reported that this is a new variant of phishing attacks seen in late 2023, which use fabricated CVEs to deceive administrators.
The attack begins with a phishing email falsely claiming the discovery of an “Unauthenticated Administrative Access” vulnerability (which doesn’t actually exist). The email includes a link to a spoofed website that uses IDN Homograph techniques to resemble the official WooCommerce site, such as using the special character “ė” in place of “e” in the domain name (e.g., woocommėrce[.]com). If the victim is deceived into downloading and installing the attached ZIP file (authbypass-update-31297-id[.]zip) as a WordPress plugin, the system proceeds to:
- Create a hidden admin account
- Exfiltrate credentials to an attacker-controlled server
- Download secondary payloads, including multiple web shells such as P.A.S.-Fork, p0wny, and WSO
- Hide both the rogue plugin and admin account from standard admin views
Once infected, attackers can remotely control the site, inject spam ads, redirect visitors to scam websites, conscript the server into a botnet for DDoS attacks, or even encrypt site data for ransom.
Experts advise WooCommerce and WordPress administrators to inspect their installations for unknown plugins or hidden admin accounts, and to regularly update their software to mitigate the risk of such attacks.
Source https://thehackernews.com/2025/04/woocommerce-users-targeted-by-fake.html
