222/68 Thursday, June 19, 2025
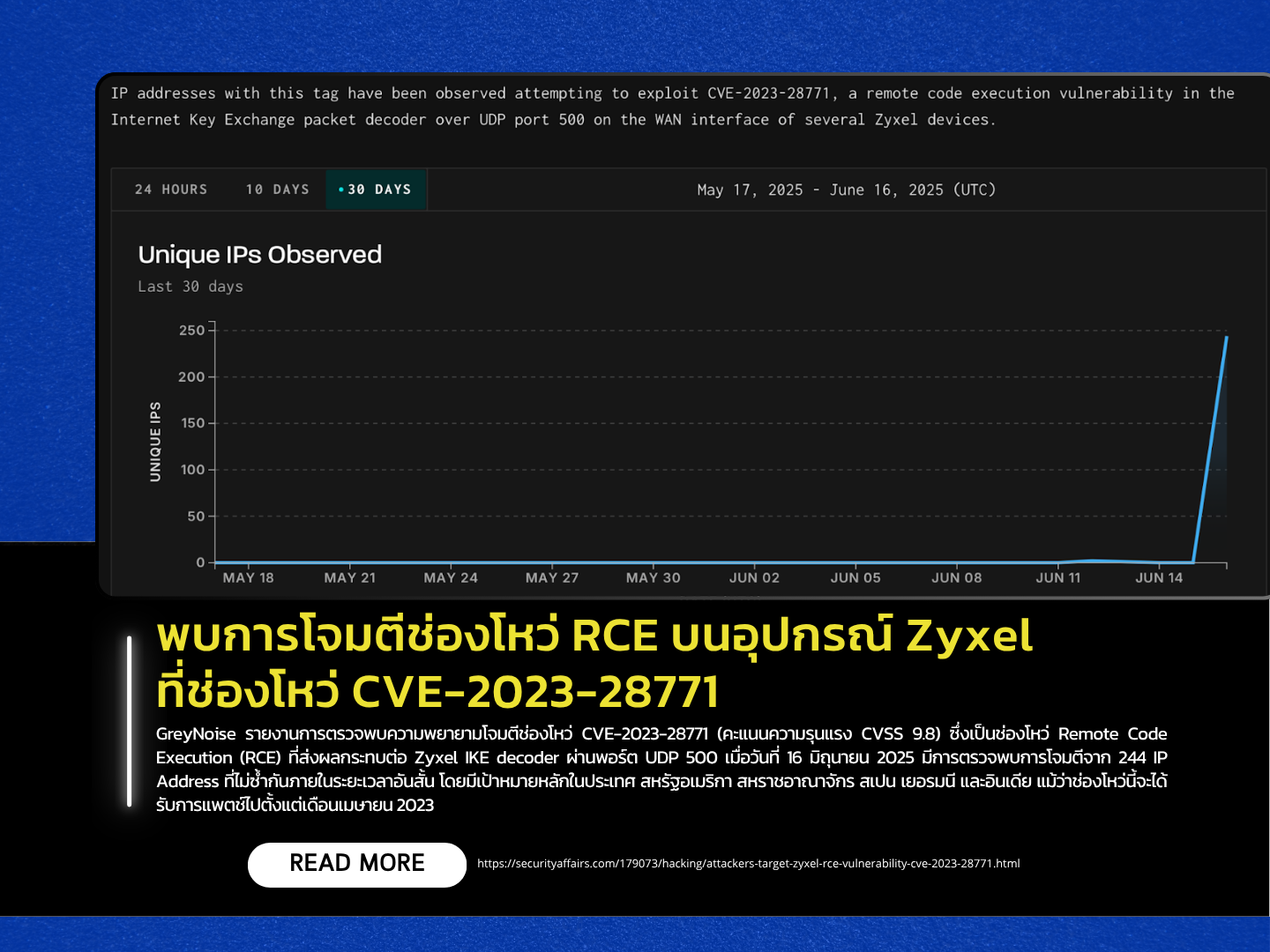
GreyNoise has reported widespread exploitation attempts targeting CVE-2023-28771, a critical Remote Code Execution (RCE) vulnerability (CVSS score: 9.8) affecting Zyxel devices’ IKE decoder via UDP port 500. On June 16, 2025, GreyNoise detected attack attempts from 244 unique IP addresses over a short timeframe, with primary targets located in the United States, United Kingdom, Spain, Germany, and India.
Although this vulnerability was patched in April 2023, GreyNoise observed a resurgence in scanning and exploitation attempts, with indicators suggesting a connection to Mirai botnet variants, as supported by VirusTotal analysis. Researchers caution that while all observed source IPs belong to Verizon Business networks in the U.S., the use of UDP port 500, which is susceptible to IP spoofing, means the true origin of these attacks remains uncertain.
GreyNoise provides the following recommendations:
- Block all 244 known malicious IPs, despite the risk of spoofing.
- Ensure Zyxel firmware is updated to the latest patched versions.
- Monitor for abnormal behavior post-intrusion, such as malware infections or signs of botnet recruitment.
- Restrict or disable UDP port 500 if not in use to reduce the attack surface.
Additionally, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2023-28771 to its Known Exploited Vulnerabilities (KEV) catalog in May 2025, confirming that the vulnerability is actively being exploited in the wild to deploy malware and take control of vulnerable network devices.
