236/68 Monday, June 30, 2025
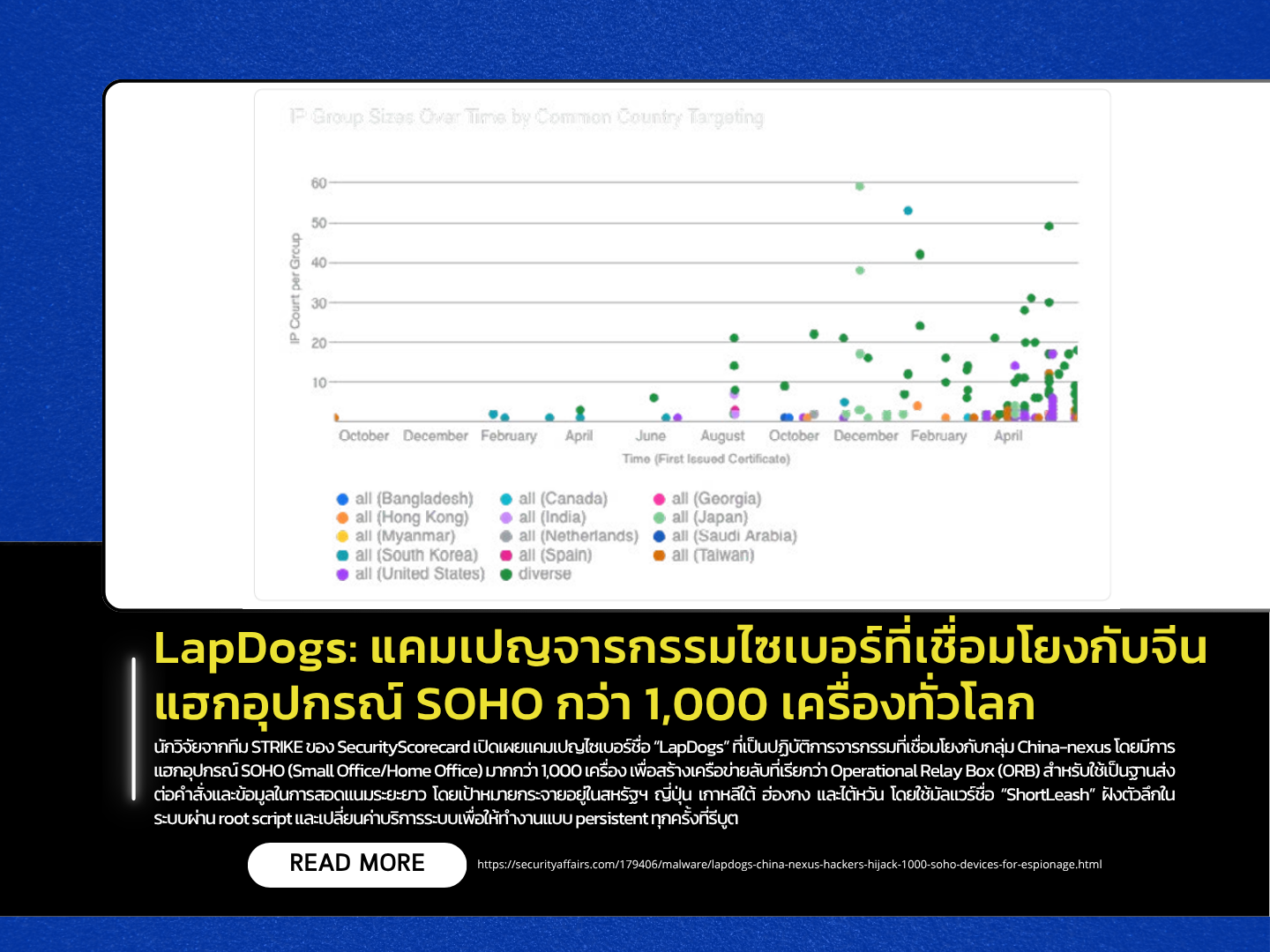
Researchers from the STRIKE team at SecurityScorecard have uncovered a cyber-espionage campaign known as “LapDogs,” which is linked to China-nexus threat actors. The operation involves the compromise of over 1,000 SOHO (Small Office/Home Office) devices, creating a covert network called the Operational Relay Box (ORB). This network is used to relay commands and exfiltrate intelligence for long-term surveillance. The campaign targets countries including the United States, Japan, South Korea, Hong Kong, and Taiwan, using a custom malware dubbed “ShortLeash.” This malware installs deeply into systems via a root script and modifies system services to maintain persistence across reboots.
The attack uses ShortLeash, a Linux-based backdoor with an installer script that requires root privileges. The script first checks if the target device is running Ubuntu or CentOS; if not, it displays a message in Chinese: “Unknown System.” If compatible, the malware disguises itself by renaming and replacing system services to evade detection and ensure persistence. The payload is double-encrypted, containing sensitive information such as certificates, private keys, and C2 URLs. It mimics Nginx server behavior and uses randomized parameters to avoid detection. LapDogs is designed to compromise a wide range of systems, including devices from ASUS, D-Link, Microsoft, Panasonic, and Synology. The malware particularly affects devices running GoAhead web server, WRT admin panel, or Microsoft IIS. Many of the affected devices also contain unpatched vulnerabilities, such as CVE-2015-1548 and CVE-2017-17663, which relate to outdated mini_httpd software.
SecurityScorecard notes that LapDogs demonstrates a high level of sophistication and is likely operated by an APT group linked to China, possibly UAT-5918. The malware contains Chinese-language code and exhibits patterns similar to past espionage campaigns targeting Taiwan. Although the exact group behind the ORB network has not been confirmed, the attacks show signs of clear intent and long-term strategic execution. System administrators are urged to assess the security of their SOHO and IoT devices immediately and enhance their detection and incident response capabilities to counter these advanced threats.
