291/68 Thursday, August 14, 2025
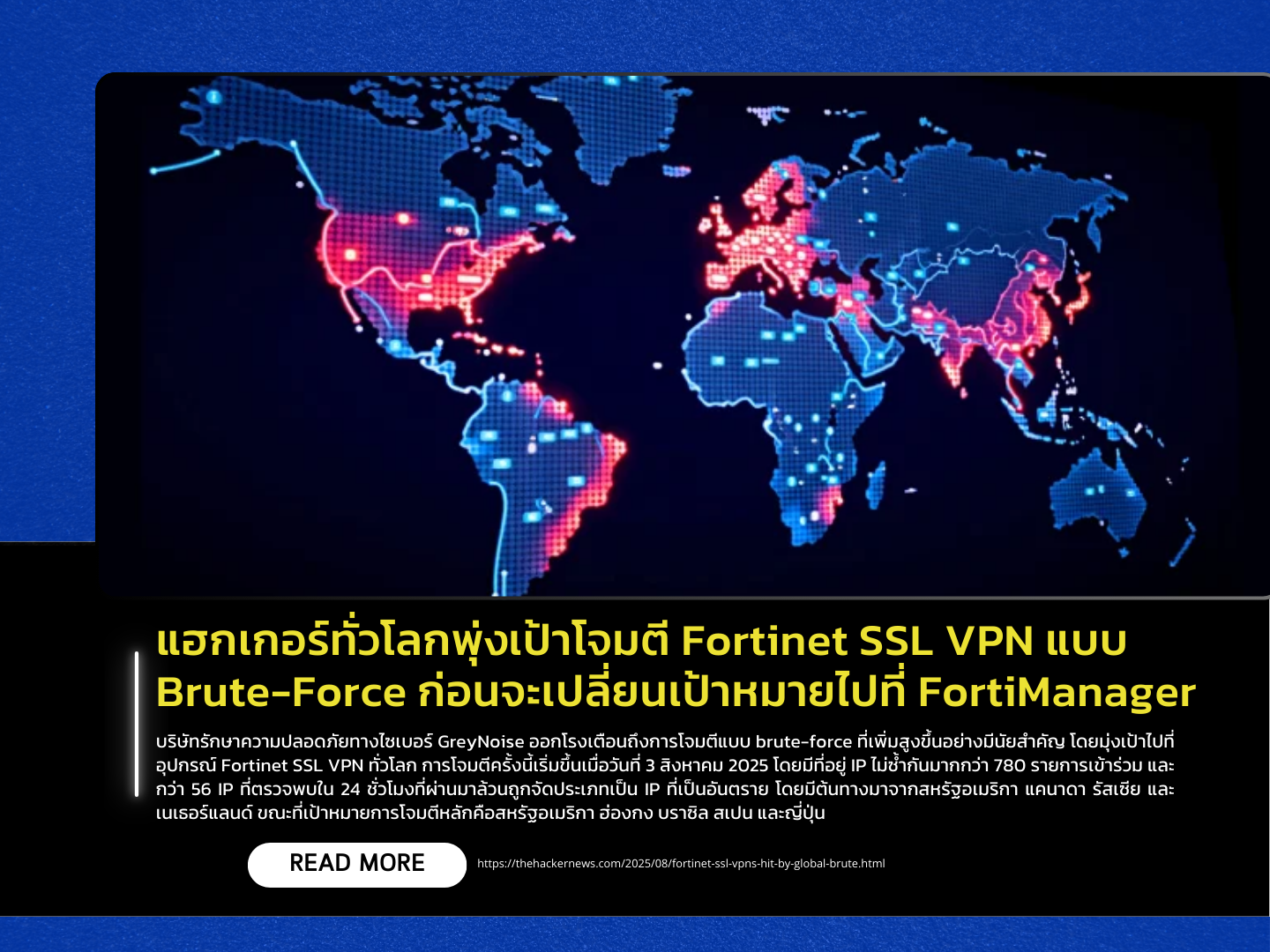
Cybersecurity firm GreyNoise has issued a warning about a significant spike in brute-force attacks targeting Fortinet SSL VPN devices worldwide. These attacks began on August 3, 2025, and involved over 780 unique IP addresses, with more than 56 flagged as malicious in the past 24 hours alone. The attack sources were primarily traced back to the United States, Canada, Russia, and the Netherlands, while the main targets included the U.S., Hong Kong, Brazil, Spain, and Japan.
According to GreyNoise, these attacks are not random but are specifically directed at Fortinet SSL VPN. The attacks have occurred in two distinct waves. The first wave involved continuous brute-force attempts using the same TCP signature. However, the second wave, observed after August 5, became more intense and targeted, with attackers employing different TCP signatures. Notably, in the second wave, the focus shifted from FortiOS to FortiManager-indicating a change in attacker behavior, likely reusing the same toolset but redirecting it to another Fortinet service.
Historical data analysis revealed a pattern: brute-force attacks like these often precede the public disclosure of new vulnerabilities (CVEs) affecting the same technologies within about six weeks. This pattern is frequently seen in enterprise-grade technologies such as VPNs, firewalls, and remote access tools-prime targets for advanced threat actors. GreyNoise’s findings serve as a crucial warning for organizations using Fortinet products to heighten vigilance and enhance their cybersecurity defenses.
Source https://thehackernews.com/2025/08/fortinet-ssl-vpns-hit-by-global-brute.html
