318/68 Tuesday, September 2, 2025
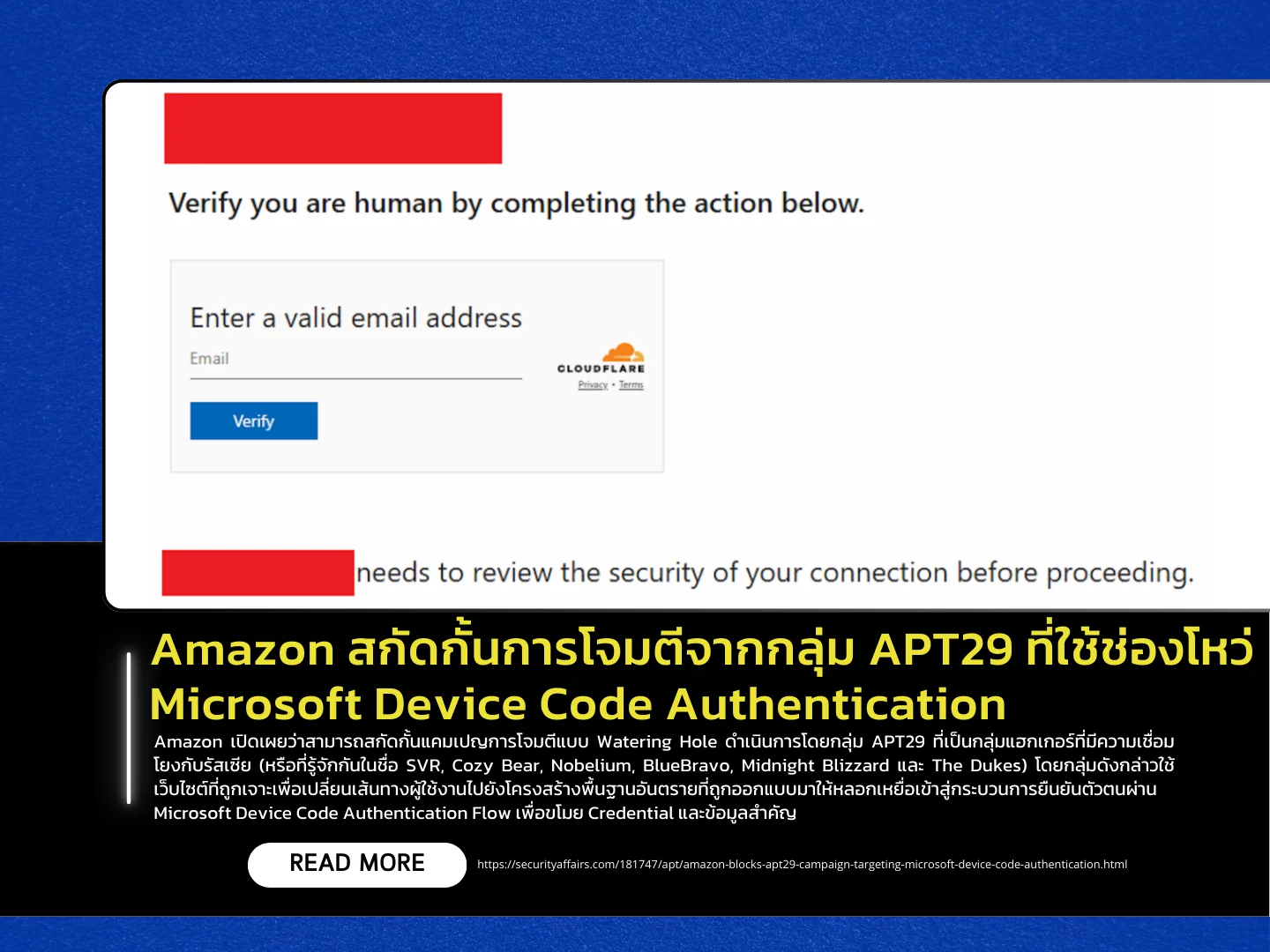
Amazon has disclosed that it successfully intercepted a watering hole attack campaign carried out by APT29, a Russian-linked hacking group also known as SVR, Cozy Bear, Nobelium, BlueBravo, Midnight Blizzard, and The Dukes. The group leveraged compromised websites to redirect users to malicious infrastructure designed to trick victims into entering their credentials through the Microsoft Device Code Authentication Flow, enabling credential theft and data exfiltration.
Researchers from Amazon Threat Intelligence found that attackers had implanted obfuscated JavaScript code into compromised websites, redirecting around 10% of visitors to malicious domains such as findcloudflare[.]com, which impersonated a legitimate Cloudflare page. The campaign employed Base64 encoding, cookie manipulation, and rapid infrastructure rotation to reduce detection. The primary targets were academics and critics of Russia, with the goal of gathering intelligence and sensitive insights.
Amazon worked closely with Cloudflare and Microsoft to disrupt the campaign, taking down malicious domains and isolating EC2 instances used as attack infrastructure. Although APT29 attempted to shift its operations from AWS to other cloud service providers, researchers were able to continue tracking and disrupting them. Reports noted that following the intervention, the attackers created new domains such as cloudflare[.]redirectpartners[.]com in repeated attempts to lure victims, showcasing the group’s evolving tactics that combine credential harvesting with supply chain-style attacks on web and cloud platforms.
