317/68 Tuesday, September 2, 2025
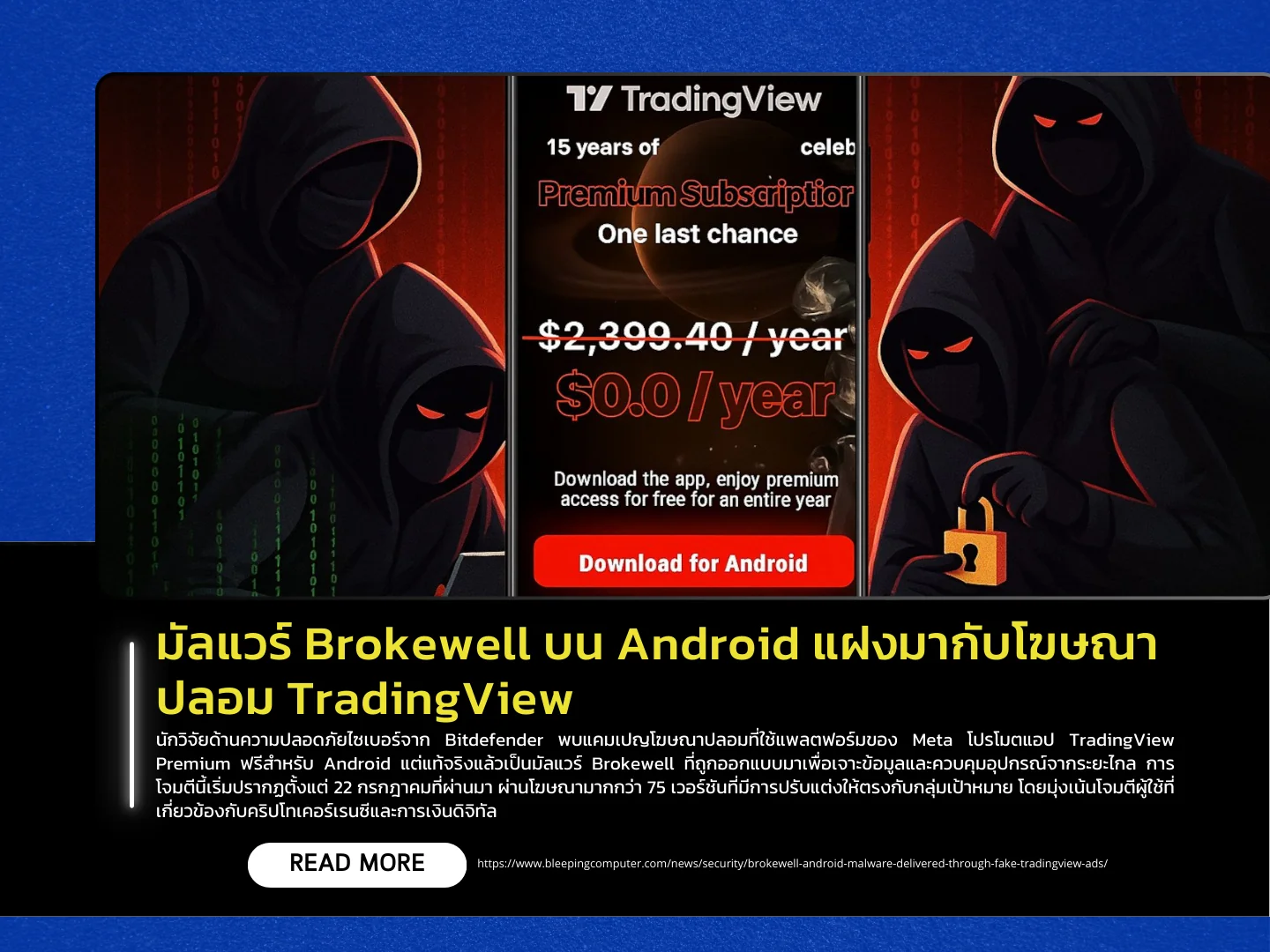
Cybersecurity researchers from Bitdefender have discovered a fake advertising campaign using Meta’s platform to promote a free TradingView Premium app for Android, which in reality is the Brokewell malware designed to steal data and remotely control devices. The campaign, which began on July 22, involved over 75 ad variations tailored to specific audiences, primarily targeting users engaged in cryptocurrency and digital finance.
When Android users clicked on the ads, they were redirected to a fraudulent website mimicking TradingView’s official page and tricked into downloading a file named tw-update.apk. Once installed, the fake app requested Accessibility permissions and displayed a fake update screen as a decoy, while in the background it granted itself full device privileges and attempted to steal the device’s screen unlock PIN by simulating an Android system update process.
Bitdefender noted that this new version of Brokewell comes with extensive capabilities, including stealing codes from Google Authenticator to bypass 2FA, capturing credentials through fake login pages, secretly recording screens and keystrokes, covertly activating the camera and microphone, and tracking the user’s location. It can also receive commands via Tor or WebSockets to send messages, make calls, uninstall apps, or even self-delete. Previously, the same network had used fake Facebook ads impersonating multiple well-known brands to target Windows systems, highlighting that this is a large-scale malware operation that is continuously expanding its attack cycle.
