361/68 Wednesday, September 24, 2025
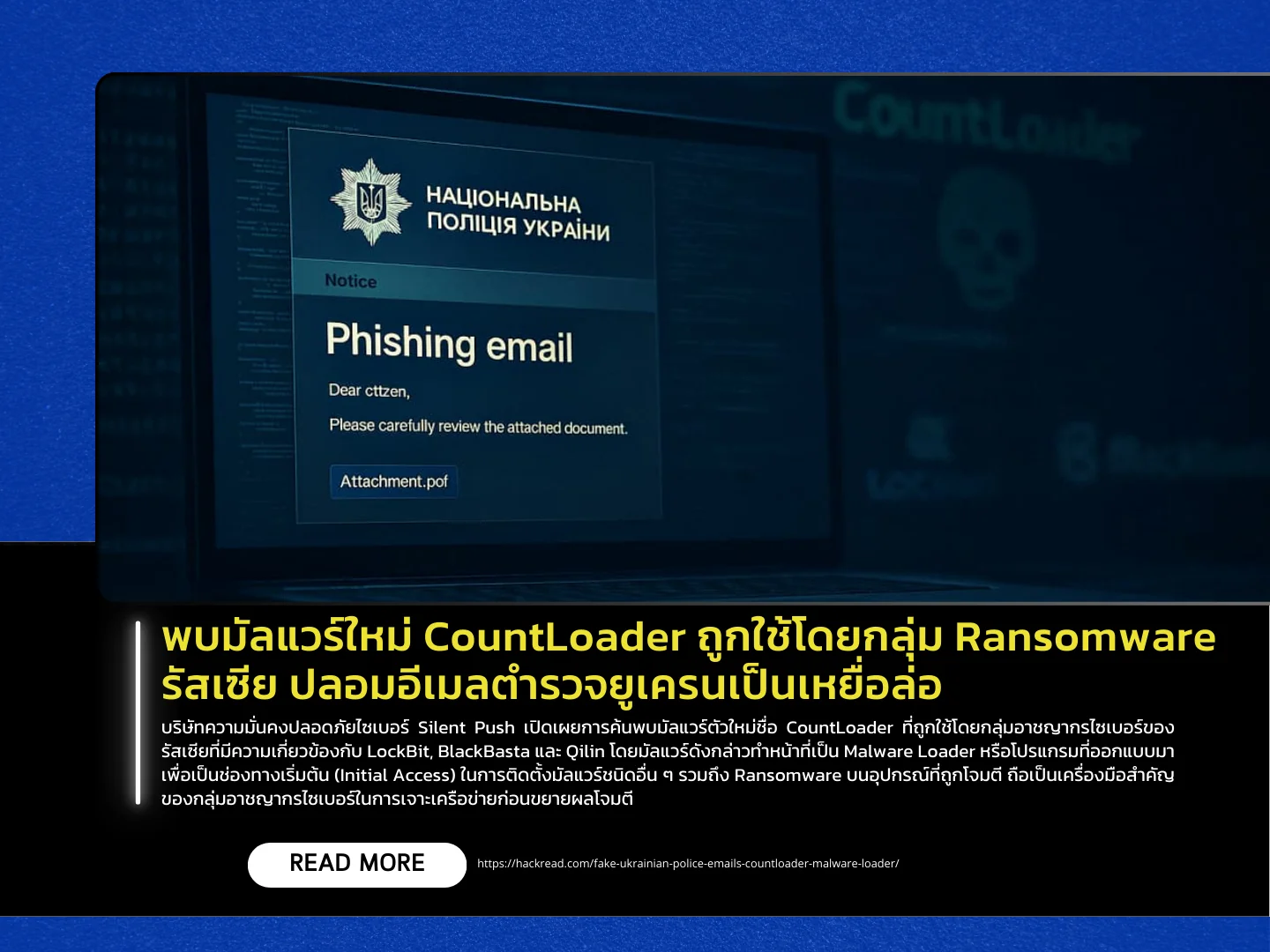
Cybersecurity firm Silent Push has revealed the discovery of a new malware strain named CountLoader, deployed by Russian cybercriminal groups linked to LockBit, BlackBasta, and Qilin. CountLoader functions as a malware loader, a program designed to serve as an initial access point for installing other types of malware – including ransomware – on compromised devices. It is considered a key tool for cybercriminals to infiltrate networks before launching full-scale attacks.
Research shows that CountLoader has been developed in three versions: .NET, PowerShell, and JScript. It can be used either by Initial Access Brokers (IABs), who sell access to compromised networks, or directly by ransomware affiliates. Recently, researchers observed a phishing campaign where attackers impersonated Ukrainian police, sending emails with malicious PDF files to lure victims into downloading and executing CountLoader, thereby paving the way for follow-on attacks.
Silent Push also found that CountLoader is tied to over 20 domains and uses digital watermarking techniques that confirm its connection to LockBit, BlackBasta, and Qilin. Additionally, one variant of the malware employs a User-Agent string mimicking the Yandex browser, a popular search engine in Russia, providing clear evidence that the threat actors are Russian-speaking. This highlights an escalation in tactics among Russian ransomware groups to infiltrate systems and inflict greater damage on their targets.
Source https://hackread.com/fake-ukrainian-police-emails-countloader-malware-loader/
