421/68 Friday, October 24, 2025
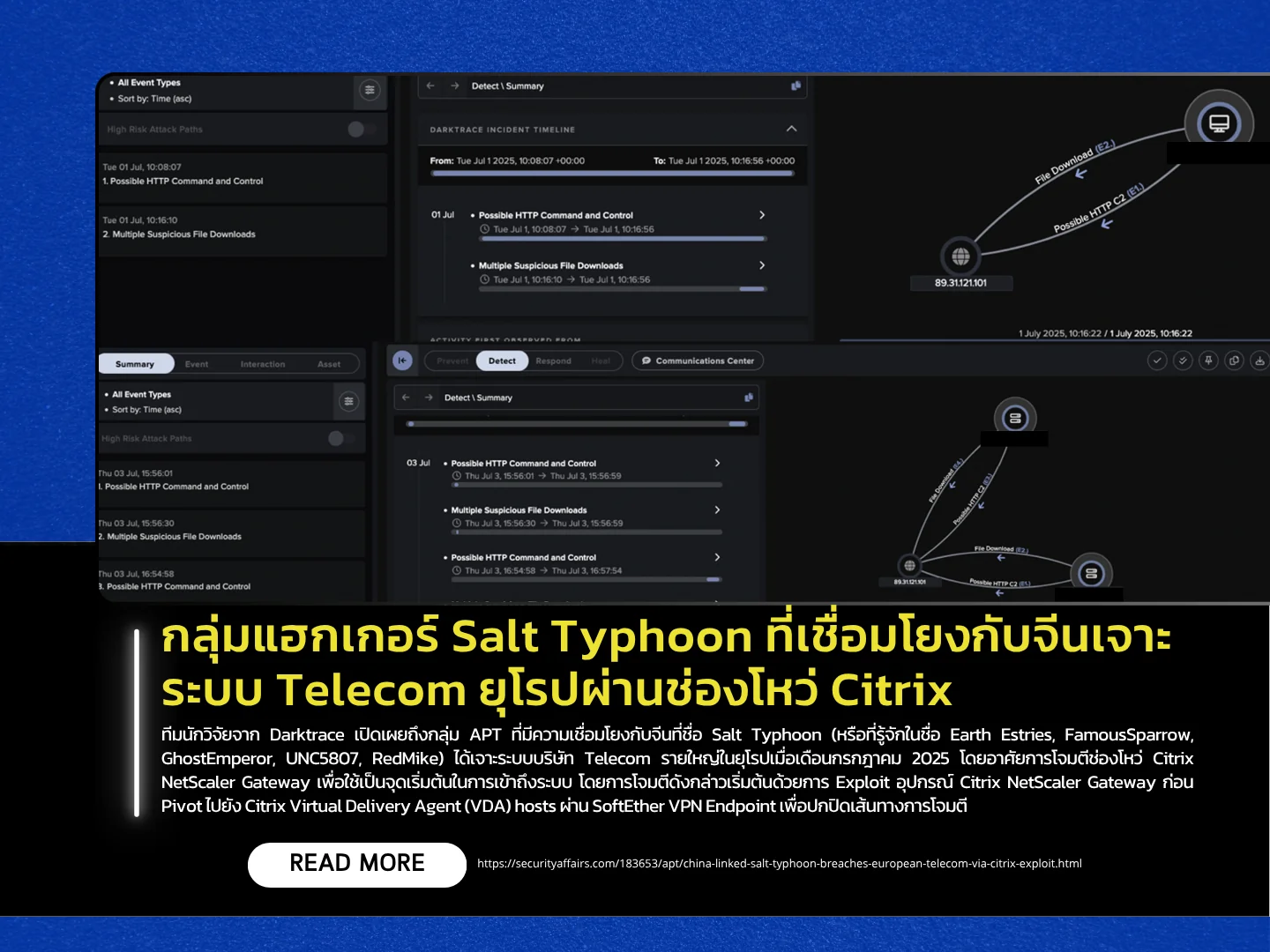
Researchers from Darktrace have disclosed that the Chinese-linked APT group Salt Typhoon (also known as Earth Estries, FamousSparrow, GhostEmperor, UNC5807, and RedMike) breached a major European telecom company in July 2025 by exploiting a Citrix NetScaler Gateway vulnerability as the initial access vector.
The attack began with the exploitation of Citrix NetScaler Gateway, followed by lateral movement to Citrix Virtual Delivery Agent (VDA) hosts via a SoftEther VPN endpoint to obfuscate attack paths. Darktrace detected that the attackers deployed SNAPPYBEE (also known as Deed RAT) using DLL sideloading, leveraging legitimate antivirus executables such as Norton, Bkav, and IObit to evade detection. The attackers also utilized LightNode VPS for Command-and-Control (C2), communicating over HTTP and an unidentified TCP protocol while disguising POST requests to mimic normal Internet Explorer traffic.
The report highlighted that the C2 domain aar.gandhibludtric[.]com (38.54.63[.]75) is directly linked to Salt Typhoon. Based on behavioral analysis, tooling, and infrastructure, the campaign shows a clear match with the group’s known tactics. This incident underscores that relying solely on signature-based security is insufficient, and organizations must deploy real-time behavioral detection systems to effectively counter Advanced Persistent Threats (APTs).
Darktrace confirmed that its AI-powered system successfully detected and mitigated the intrusion before the attackers could escalate privileges. Experts assess with moderate confidence that Salt Typhoon/Earth Estries was behind the operation, reinforcing the group’s capabilities and its ties to state-sponsored cyber operations.
