04/69 Tuesday, January 6, 2026
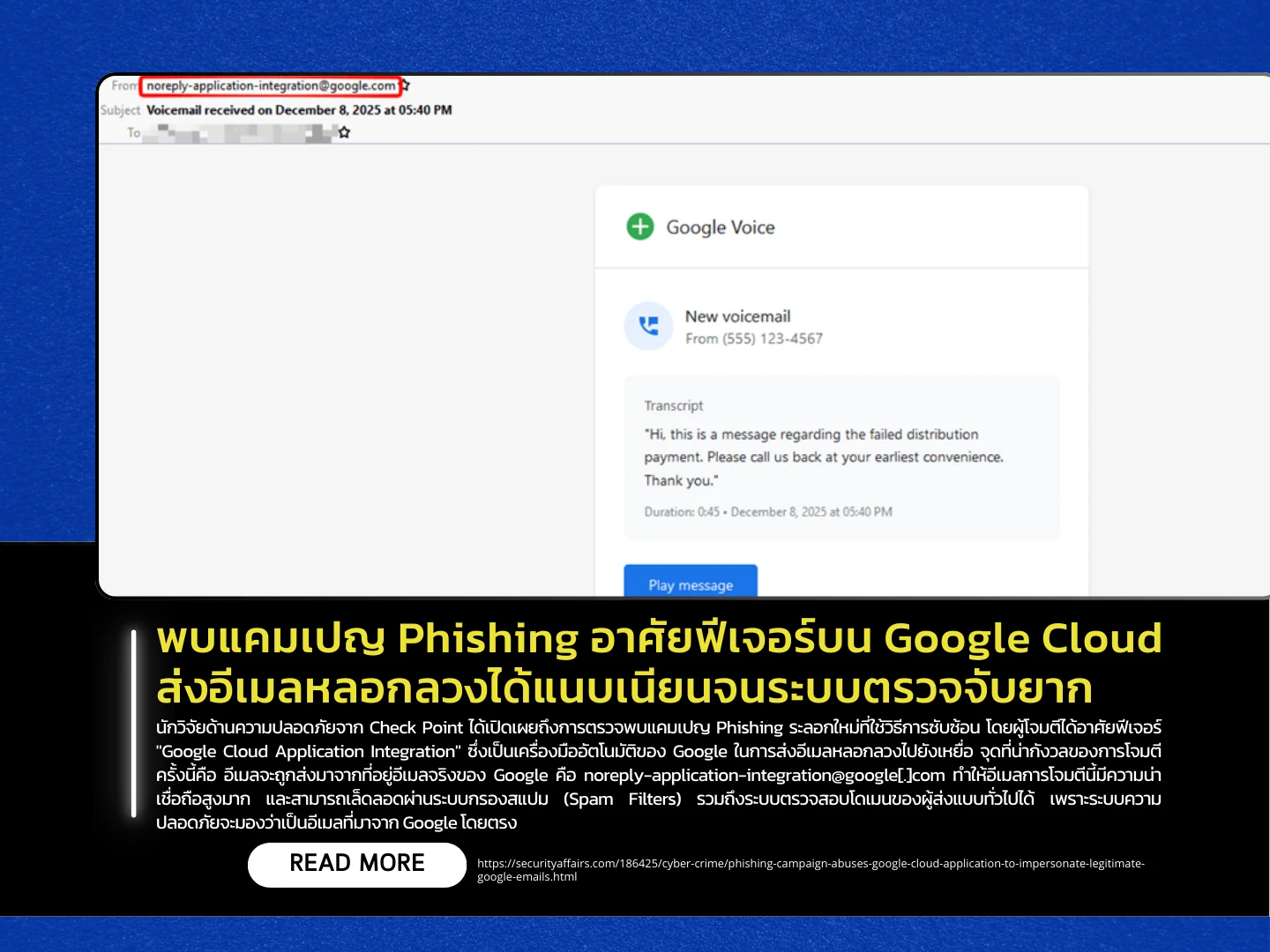
Cybersecurity researchers from Check Point have revealed a newly discovered phishing campaign that employs a sophisticated technique by abusing Google Cloud Application Integration, an automation feature provided by Google, to send fraudulent emails to victims. What makes this campaign particularly concerning is that the phishing emails are sent from a legitimate Google email address — noreply-application-integration@google.com — giving them a very high level of credibility. As a result, these emails are able to bypass spam filters and common sender-domain verification mechanisms, since security systems perceive them as originating directly from Google.
The attack begins with emails that closely mimic legitimate Google notifications, such as voicemail alerts or document-sharing messages, designed to entice victims into clicking embedded links. Once clicked, the attack chain uses multi-stage redirection techniques. The initial link points to a seemingly legitimate and trusted domain on storage.cloud.google.com, helping establish trust. Victims are then redirected to a fake CAPTCHA page intended to evade automated security scanning, before ultimately being sent to a fraudulent Microsoft login page hosted on a non-legitimate domain, where credentials are harvested. Researchers observed that more than 9,400 phishing emails were sent within a two-week period, primarily targeting the manufacturing, technology, and financial sectors.
Google has since confirmed awareness of the campaign and stated that it has already taken action to block the abuse. The company clarified that the incident resulted from threat actors misusing Google’s workflow automation tools, rather than a compromise of Google’s infrastructure itself. This case highlights an important security lesson: even emails sent from trusted cloud service providers can be abused for phishing purposes. Organizations and users are therefore urged to exercise heightened caution when reviewing links and notification emails, even when the sender appears to be a legitimate and trusted source.
