40/69 Thursday, January 22, 2026
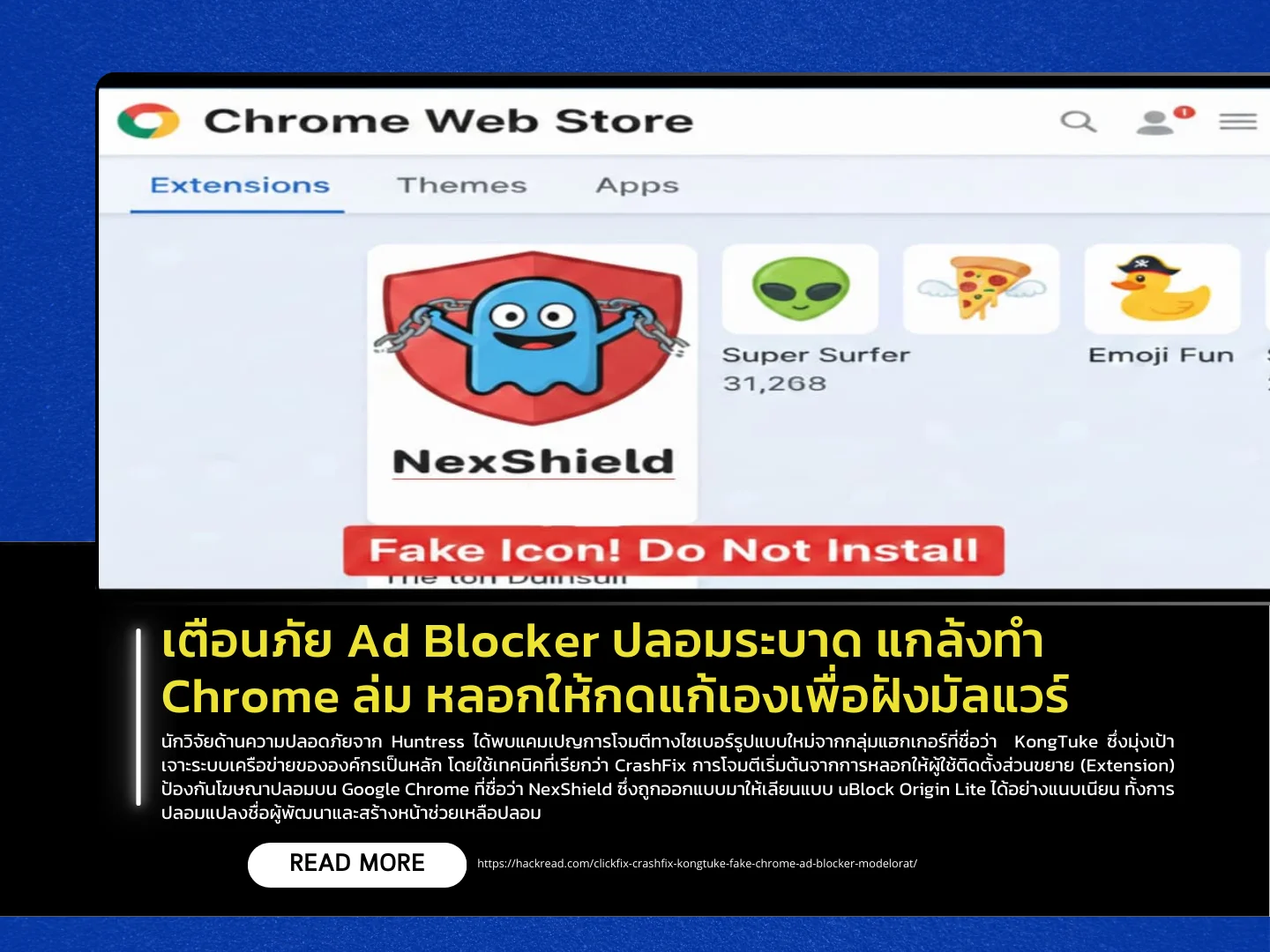
Security researchers from Huntress have identified a new cyberattack campaign linked to a threat group known as KongTuke, which primarily targets corporate networks. The attackers use a technique dubbed “CrashFix.” The attack begins by luring users into installing a fake ad-blocking browser extension on Google Chrome called NexShield, which is carefully designed to impersonate uBlock Origin Lite. The extension forges developer details and hosts a fake support page to appear legitimate. Once installed, the extension lies dormant for about 60 minutes before executing a script that floods the victim’s system with connection requests (a local DoS), exhausting system resources and causing the browser to freeze and crash.
When users attempt to relaunch the browser, they encounter the next stage of the trap: a fake security alert claiming that the browser crashed abnormally and that a security issue has been detected. The message provides step-by-step “manual recovery” instructions, prompting the user to press Win + R, then Ctrl + V, and hit Enter. In reality, the attackers have already planted a malicious command in the clipboard. This command abuses a legitimate Windows utility called finger.exe (renamed to ct.exe) to download and install malware on the system.
The payload delivered is ModeloRAT, a Python-based backdoor malware that gives attackers covert access to steal sensitive corporate files and credentials. The malware disguises itself in the process list under benign-looking names such as Spotify47 or Adobe2841. ModeloRAT also includes anti-analysis capabilities: if it detects security tools or sandbox environments-such as Wireshark-it may terminate execution or return deceptive responses to avoid investigation. Experts advise users to carefully verify extension developers and to treat any browser crash followed by instructions to run command-line fixes as an immediate red flag indicating a malicious trap.
Source https://hackread.com/clickfix-crashfix-kongtuke-fake-chrome-ad-blocker-modelorat/
