72/69 Thursday, February 5, 2026
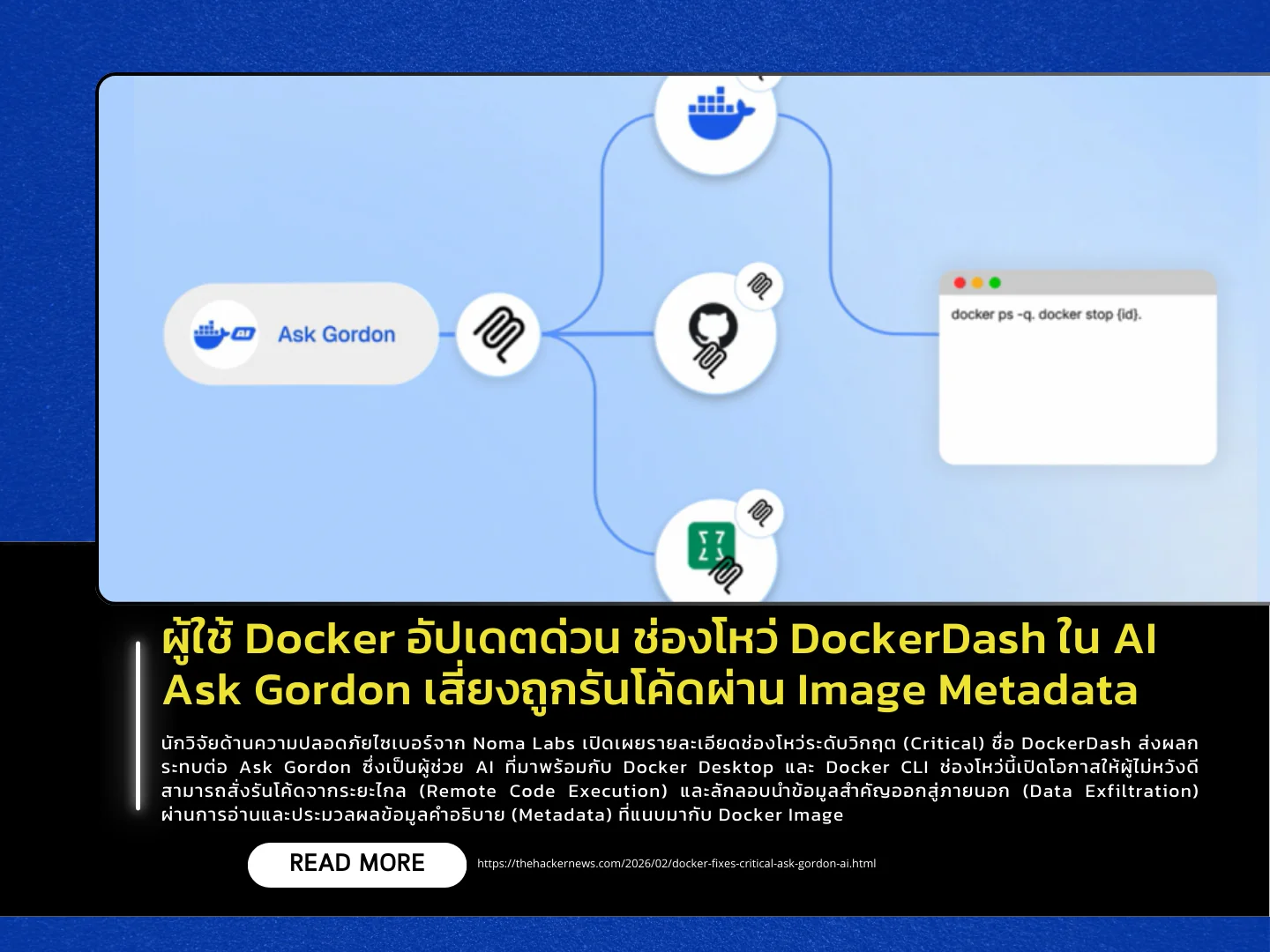
Cybersecurity researchers from Noma Labs have disclosed a critical vulnerability named DockerDash affecting Ask Gordon, the AI assistant integrated into Docker Desktop and Docker CLI. The flaw allows attackers to perform Remote Code Execution (RCE) and secretly exfiltrate sensitive data by exploiting how the assistant reads and processes metadata attached to Docker images.
The attack begins with a malicious Docker image that embeds harmful commands within the LABEL field of a Dockerfile. When a user queries Ask Gordon about the compromised image, the hidden instructions are forwarded to the MCP Gateway, prompting various tools to execute them with the user’s privileges. This could enable attackers to compromise cloud and CLI environments or access desktop-side data such as configurations, container details, and internal network information.
Docker addressed the vulnerability in version 4.50.0, released in November 2025, which also fixed a separate prompt injection issue reported by Pillar Security. Researchers emphasize that this incident highlights growing AI supply chain risks, where manipulated input data can serve as an attack vector. Users are strongly advised to upgrade to the latest version immediately and avoid using images from untrusted sources.
Source https://thehackernews.com/2026/02/docker-fixes-critical-ask-gordon-ai.html
