84/69 Wednesday, February 11, 2026
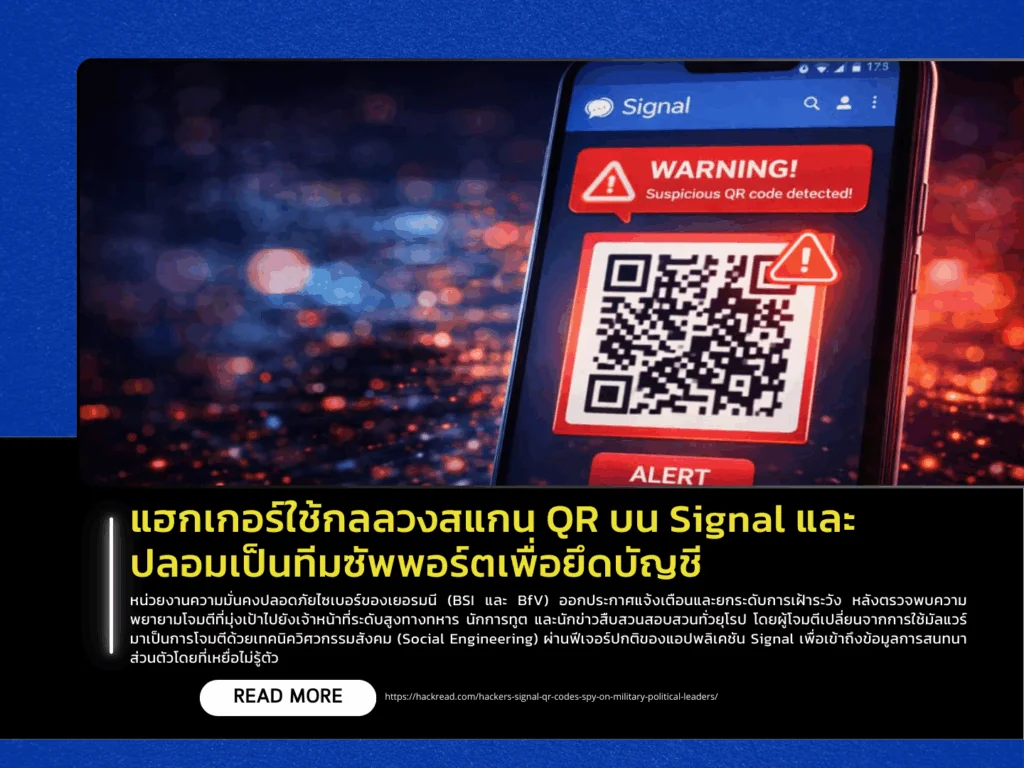
Germany’s cybersecurity authorities, including the Federal Office for Information Security (BSI) and the Federal Office for the Protection of the Constitution (BfV), have issued a warning and heightened surveillance after detecting targeted attack attempts against senior military officials, diplomats, and investigative journalists across Europe. Attackers have shifted from malware-based methods to social engineering techniques, abusing legitimate features of the Signal application to gain access to private conversations without victims’ awareness.
Two primary attack methods have been identified. The first is a fake support scam, in which attackers impersonate Signal’s support or security team-sometimes using chatbots-and claim there has been a data breach to pressure victims into providing their six-digit PIN or SMS verification code. This enables attackers to take over the account and lock the legitimate user out. The second method involves malicious QR codes. Victims are tricked into scanning a QR code under the pretense of accessing documents or joining a group, but the code actually links the attacker’s device to the victim’s account via the “Linked Devices” feature. This approach is difficult to detect because victims can continue using the app normally while attackers gain access to past chat history and incoming messages.
To mitigate these threats, experts advise users to ignore messages claiming to be from support, as Signal does not send private messages requesting PINs or verification codes. Users should regularly review the “Linked Devices” menu in their settings and remove any unfamiliar devices. Enabling the “Registration Lock” feature is also recommended, as it requires the user’s PIN before a new device can register the account, reducing the risk of account takeover even if an attacker obtains the SMS verification code.
Source https://hackread.com/hackers-signal-qr-codes-spy-on-military-political-leaders/
