42/69 Thursday, January 22, 2026
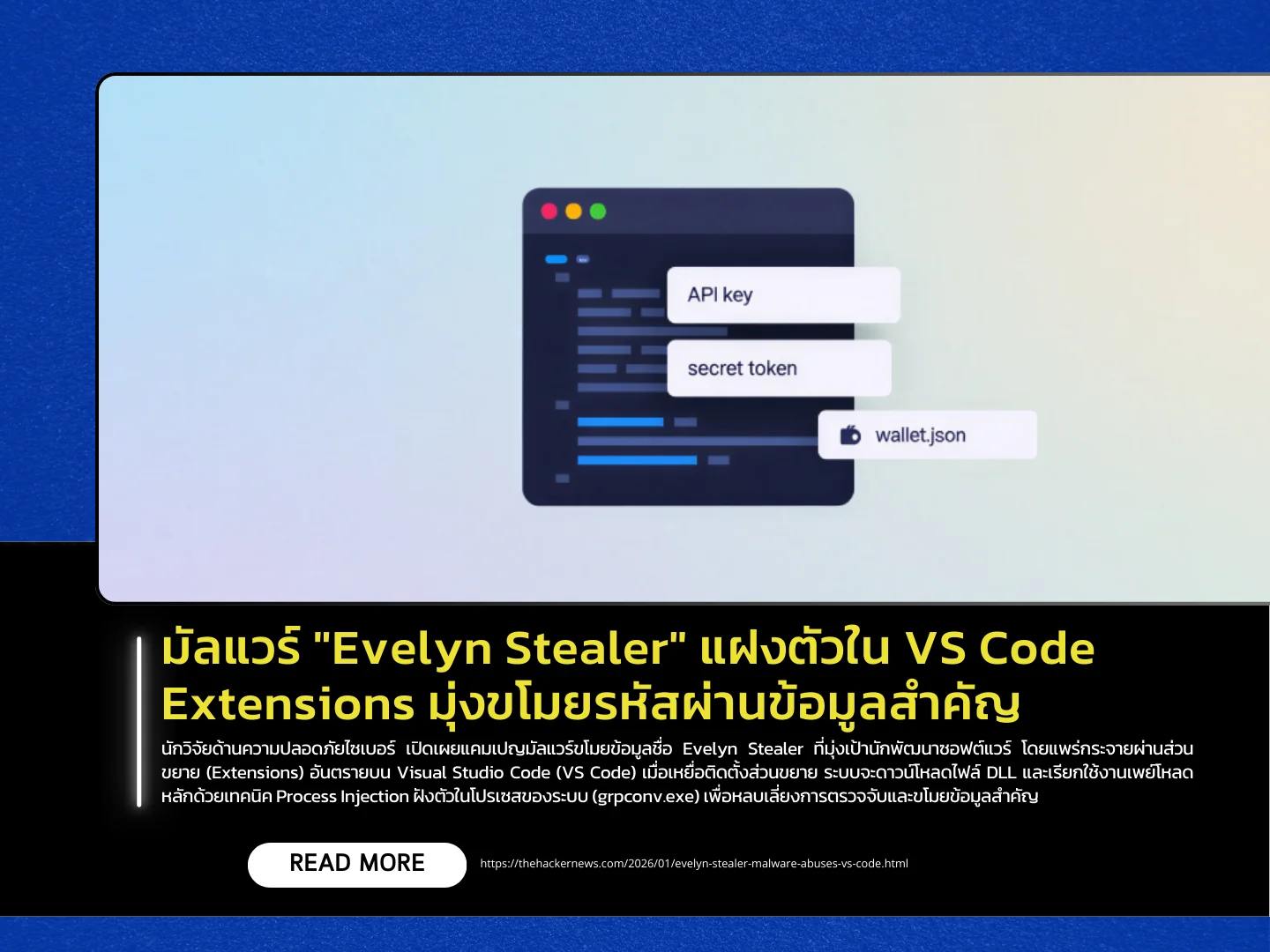
Cybersecurity researchers have disclosed a data-stealing malware campaign dubbed Evelyn Stealer, which specifically targets software developers by spreading through malicious extensions on Visual Studio Code (VS Code). Once a victim installs a compromised extension, the malware downloads a malicious DLL and executes its primary payload using process injection, embedding itself into a legitimate system process (grpconv.exe) to evade detection and steal sensitive information.
The malware is capable of collecting a wide range of data, including passwords, browser cookies (from Chrome and Edge), cryptocurrency wallets, Wi-Fi credentials, screenshots, and clipboard contents. It manipulates browsers via command-line control and applies stealth parameters-such as --no-sandbox and --disable-logging—to minimize user disruption and bypass security mechanisms, enabling session data extraction. The stolen data is then compressed into a ZIP archive and exfiltrated to the attacker’s server via FTP.
In addition to Evelyn Stealer, researchers also identified two other Python-based information stealers: MonetaStealer, which targets Apple macOS systems, and SolyxImmortal, which focuses on data theft via Discord webhooks. These findings highlight a growing trend of threats targeting developer environments as an initial foothold for broader intrusions into cloud infrastructure and enterprise networks. Organizations are advised to tighten controls on third-party extension installations, enforce strict approval processes, and regularly review access privileges to mitigate these risks.
Source https://thehackernews.com/2026/01/evelyn-stealer-malware-abuses-vs-code.html
