54/69 Wednesday, January 28, 2026
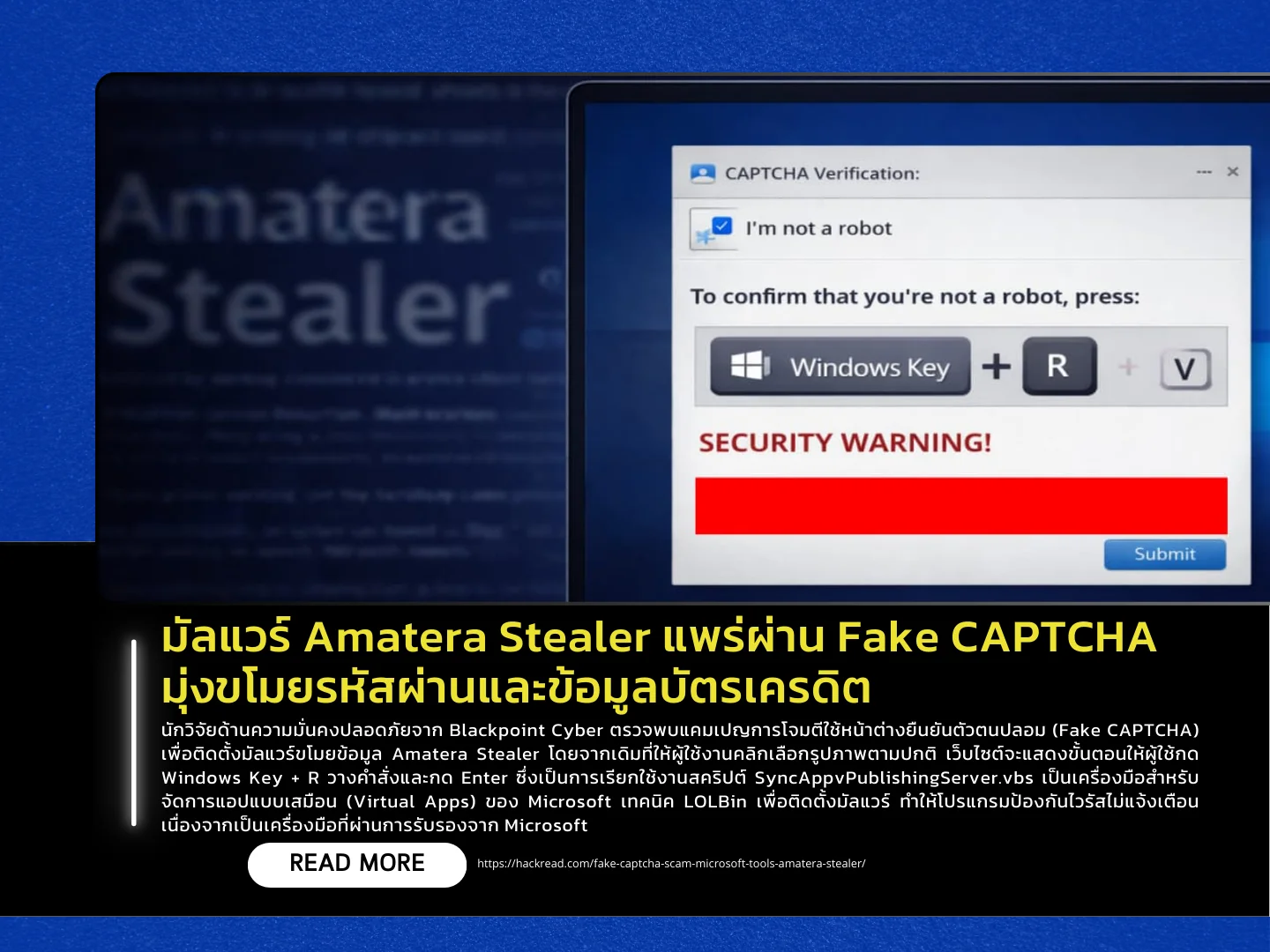
Cybersecurity researchers from Blackpoint Cyber have identified an attack campaign that uses fake CAPTCHA prompts to install the Amatera Stealer infostealer malware. Instead of asking users to select images as in legitimate CAPTCHA challenges, the malicious website instructs victims to press Windows Key + R, paste a command, and press Enter. This action executes the script SyncAppvPublishingServer.vbs, a legitimate Microsoft tool used to manage virtual applications (App-V). The attackers abuse this LOLBin (Living-off-the-Land Binary) technique to install malware without triggering antivirus alerts, as the tool is trusted and digitally signed by Microsoft.
The campaign also employs multiple anti-analysis and evasion techniques. Commands are retrieved from Google Calendar (.ics) files, while PNG image files downloaded from public hosting services such as Imgur conceal malicious code using steganography. In addition, the script checks whether it is running in a sandbox or virtualized environment; if anomalies are detected or no real user interaction is observed, the malware terminates itself immediately to avoid analysis.
The final stage of the attack installs Amatera Stealer, which is designed to exfiltrate stored passwords, credit card information, and browser data. This threat affects Windows 10, Windows 11, and Windows Server systems that have the App-V feature enabled. Researchers strongly advise users never to copy and paste commands from websites into the Windows Run dialog. Legitimate CAPTCHA challenges do not require opening the Run window or executing commands; encountering such instructions should be treated as a clear warning sign, and the process should be stopped immediately.
Source https://hackread.com/fake-captcha-scam-microsoft-tools-amatera-stealer/
